- includes detailed discussion of crafting longer passwords and techniques to remember passwords

| IDENTITY
THEFT
- includes detailed discussion of crafting longer passwords and techniques to remember passwords |
 |
see
also witiger.com/ecommerce/hackers.htm
see
also witiger.com/ecommerce/hackersvideo.htm
see
also witiger.com/ecommerce/SocialEngineering.htm
see
also witiger.com/ecommerce/scams.htm
see
also witiger.com/ecommerce/domainnamephishing.htm
| . | This page
used in the following courses taught by Prof. Richardson
.
|
 |
Before reading
through this unit, you might be interested in listening to the CBC Radio
interview that I gave in March 2006 about aspects of Identity Theft.
It provides a good overview of the situation.
The interview runs about 9 minutes. There are 3 file sizes you can download, depending on how fast your internet connect is. WTGR |
 |
Prof. Richardson discussing
Identity Theft in a 2008 documentary on the iChannel
Part 1
|
 |
YES THIS PAGE IS USEFUL
Nov 2011 - former UTSC student
(MGTD06
in 2008) Hasan Shahzad stopped by to talk about his work in Mutual Funds
at Royal Bank and mentioned that frequently he references material from
this page in order to educate clients as to some risk and threat situations
they should be careful about regarding identity theft and hacking.
Thanks Hasan for mentioning
this.
|
| LEARNING
OBJECTIVES |
After completing
reading this unit, and listening to the lecture in class, student will
have information about:
o How
to fight identity theft- Cdn Govt Resources
|
| INTRODUCTION | Identity theft
is not a new problem - it has been around before the WWWeb became popular
in the late 1990's and early 2000's - but since the advent of many activities
on the Web requiring people to sign up, log in, register to view, etc,
- there has been an explosion in the number of situations where such personal
profile information is stolen and abused. The circumstances of using the
Web on a personal basis have resulted in many people surrendering identity
information to companies and organizations in a way which is not secure
and what is more problematic - the surrendering is done to people to whom
they have no recourse to complain.
Warning Identity Theft is not just a "technical hack" - in a large number of identity theft cases, the victim knows the perpetrator, it often is a distant family member, casual friend, someone who has access to your home, etc. Many cases of identity theft have been reported by women who had an ex-boyfriend use their credit card fraudulently, or husbands who had their ex-wive continue to use their credit card number.WTGR |
 |
Social Engineering
x University of Toronto (UTM) students Wyann L. and Sol. L in MGD 415 in March 2008 created a kewl video in which they describe several components of how Social Engineering tricks can lead to an Identity Theft situation. If you watch the video carefully, you can pick up on several tricky (but convincing) lies that are told. And,,, what makes it even trickier is that the tricky lines come from a friend - which makes it less likely the "victim" will be suspicious. youtube.com/watch?v=9qKfrnXjqjc While it is sensational to talk about Identity theft happening by strangers hacking you. it is far more common for it to be committed by someone you actually know. |
 |
Social Engineering / Identity Theft
- example of 2 techniques
1 - cross contamination re: RFID 2 - skimming Credit Cards x University of Toronto (UTM) students in MGD415 in early April 2009 Altin E, Trevor G Mark Teh-Yu H, Gianmarco R Nicholas S, Tiffany (Wutang) W. created an informative video in which they mixed in Social Engineering tricks and Skimming which lead to an Identity Theft situation. youtube.com/watch?v=te6ULbUpuRQ also posted at www.bollytainment.com/tags/Witiger |
| The premise of the video is "friends" are not friends when they use your credit card dishonestly - it is better to be more careful with your cards and never let anybody use them. |
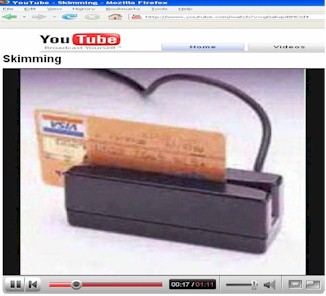 |
Identity Theft - Credit Card
Skimming
x University of Toronto (UTM) students Bashir K., and Jawad K., and Nomaan C. in MGD 415 in March 2008 created a kewl video in which they describe several components of how Skimming a credit card can lead to an Identity Theft situation. Watch the video carefully. youtube.com/watch?v=g0akqoBMOd4 Often skimming is done at gas stations or restaurants, since those are the places that hire people who work for minimum wage, - and many times such businesses don't bother doing background checks cause the employees are mostly part-timers. |
| Skimming Prevention Tips
1. I (WTGR) always pay cash at gas stations, it is faster to lay down one or two twentys instead of waiting in line anyway - and with gas prices so high, nobody puts a lot of gas in anyways these days. 2. If you do use the card, don't let the attendant take it out of your hand (sometimes they just rudely grab it) and swip it on their keyboard, insist on swiping it on the terminal passed to customers. 3. At restaurants, don't put your card on the little tray they sometimes bring out, instead, walk back to the cash register and swipe it yourself, this way you can make sure it is not being swiped twice. |
 |
Identity Theft - Credit Card
Fraud
- description of frauds and tips to prevent this youtube.com/watch?v=2CfM-KLuvEs xDone by students - done by students Richard L. and Steven L. in BCS 555 at Seneca College in November 2011 |
www.theepochtimes.com |
During the 1st week of October 2007, Richardson was interviewed by Joan Delaney for the English-Canada version of the international newspaper The Epoch Times. The story was about Identity Theft and associated circumstances such as viruses, hacking and social engineering |
| Richardson was quoted saying "one of the reasons identity theft is on the rise is the ease with which intruders can hack into people's computers. Think about guns for example; … can you imagine what would happen if you're walking down the street and guns are lying on a ditch and there's an arrow that says here's the bullets and there's another little arrow that says here's how to load it? Well, this is the problem with the Internet," says Richardson. "There are many websites where people can download simple hacking software and then use it to hack people, and then [there are] instructions in chat rooms and message boards about how to do hacking, and there is no law against that." " |
 |
During
the 2nd week in February 2007, Richardson was a guest expert on the
Bill Good Show on CKNW Radio in Vancouver.
o http://people.senecac.on.ca/tim.richardson/audio/CKNW-Bill-sinNumbersFeb2007seg1.mp3 o http://people.senecac.on.ca/tim.richardson/audio/CKNW-Bill-sinNumbersFeb2007seg2.mp3 Richardson was interviewed about Identity Theft issues in the context of the recent report of the Auditor General and the study by the Fraser Institute www.fraserinstitute.ca. |
| WTGR explained that companies recognize that mass marketing to new customers is not as effective as focusing on building a business by selling more to existing customers. Compaines then focus more on gathering detailed profile information on existing customers in order to up-sell and cross-sell products, and by collecting such information (birthdates, credit card numbers, home addresses etc.), put customers in a position of vulnerability when such databases become compromised. CKNW is part of the CORUS radio network. |
 |
Fraser
Institute www.fraserinstitute.ca.
It has been discovered that there is a lot of management and fraud within
Canada's Social Insurance Number systems and this is leading to speculation
about how fraudulent identities are costing the government and private
sector.
"... reports by the Auditor
General show there are 2.4 million more social insurance numbers than actual
Canadians,”
|
| Identity
Theft Risks
|
Koprowski writes "...even as companies implement more IT security to prevent Internet hackers from tapping their networks, there will be increased theft of secure data by insiders, like employees." Koprowski quotes Joseph Ansanelli, chief executive officer of the data security firm Vontu. Ansanelli says "Many retailers have not educated their employees on the value of customer information to the company, nor have they educated them on employee responsibilities towards protecting and correctly handling this information." permission to quote from ecommercetimes.com given by publisher Richard Kern in an email Dec 10th, 2004. Prof. Richardson is also a contributing writer to ecommercetimes.com. Copies of emails kept on file in the permissions binder. |
A huge resource site about identity theft "Identity theft is a crime in which an imposter obtains key pieces of information such as Social Security and driver's license numbers and uses it for their own personal gain. Identity theft takes many forms. Almost all cases, victims are left with a ruined credit or criminal history and the complicated task of regaining their good names. Identity theft is an evolving crime and criminals are finding new and more sophisticated ways to steal and use information. " William Yau says - "the site is a huge resource centre about identity theft. It has things from current laws to victim's resources. This site pretty much tells you what you need to know, what to do if you are a victim, or even just wanting to learn more about the topic." |
| .KEY
POINTS |
The Canadian federal government considers Identity Theft a serious and growing problem and has devoted resources to educating the public and providing information to help people understand their risk. |
How to fight identity theft
.
| RCMP | The Royal Canadian Mounted
Police have an extensive website which discusses many aspects of Identity
Theft security and risk situations.
http://www.rcmp-grc.gc.ca/scams/index_e.htm |
| Identity
Theft - government resources |
click on this screen capture
to go to the RCMP government website
see http://www.rcmp-grc.gc.ca/scams/identity_theft_e.htm |
Contact was made May 17th, 2005 with Michelle Corrigan, and May 19th w Constable P. Flood, of the Public Affairs branch and June 6th with Constable Cyndy Henry of the Intellectual Property office of the RCMP HQ in Ottawa regarding permission to link, and use this screen capture. Copies of emails kept on file in the permissions binder.
| Identity
Theft - problems raised by government jurisdictional issues |
While
nobody would accuse the government of aiding Identity Theft, and there
is lots of ways the government is trying to inform people of Identity Theft
risk and threat situations, one fact remains that governments are based
on political borders -and therefore law enforcement agencies are based
on political borders: - cybercrime is borderless.
Sometimes, matters of jurisdictional issues make it difficult for law enforcement officials to track identity theft cases and red tape between jurisdictions makes it difficult to trace leads quickly enough to catch "bad guys" Nicole Stampatori, national
practice leader of security, identity and privacy at IBM Canada was quoted
in ComputerWorld Canada in May 2006 saying
Rene Hamel, ex-RCMP officer said cooperation between different law enforcement agencies isn't easy, even within Canada's borders. Hamel explained "... if an identity theft of a Toronto resident is perpretrated by a thief in Vancouver, it is unclear whether the crime should be investigated by the Toronto or Vancouver police. Stampatori and Hamel quoted May 26th, 2006 by Rosie Lombardi for ITworldcanada.com - publisher of ComputerWorld Canada |
| Identity
Theft - problems raised by government jurisdictional issues |
Rene
Hamel, ex-RCMP officer
"Time consuming jurisdictional issues can become very troublesome in cases of international crime. International investigations are governed by the MLAT - Mutual Legal Assistance Treaty which is an agreement between two countries to exhange information, enforce criminal laws and apprehend criminals." Hamel explains "if information is stolen from a Canadian database by someone in China, you have to go through this long process to get information". Stampatori and Hamel quoted May 26th, 2006 by Rosie Lombardi for ITworldcanada.com - publisher of ComputerWorld Canada |
| This 2002 article by Ellen
Roseman, in the Toronto Star, outlines the main points for consideration
and you are encouraged to read it through thoroughly. It applies just as
easily in 2006 as in 2002.
One of the key points is that Identity theft is not, strictly speaking, an internet / e-commerce crime but it is increasingly perpetrated by people using the internet and gathering information through e-commerce situations which are fraudulent. |
| Story
About How Identity Theft Happened to one Victim |
"Identity
Thieves Prey on Slack Mail Security"
article by Ellen Roseman 2002 April 20th "IDENTITY THEFT occurs when someone appropriates your personal information without your knowledge to commit fraud. Criminals may steal your credit card number, driver's license number, social insurance number and other key pieces of your identity. They use this information to impersonate you, spending as much money as they can in as short a time as possible before moving on to someone else's name and account information." |
| Story
About How Identity Theft Happened to one Victim
|
Roseman write "The Toronto woman (who asked us not to use her name) wrote to Equifax Canada Inc. in early January, asking to see her credit record. It never arrived. A month later, Equifax wrote to say her credit record had been sent out on Jan. 14. Had she received it? "When I called on Feb. 25," the woman recalls, "they confirmed that some Equifax credit reports had been intercepted fraudulently, that they were investigating the problem and had put a note on my credit file that said `protecting my information.'" When the second credit report hadn't arrived by March 21, she called and found it had been stolen again. Then, on March 24, her credit card was declined when she tried to pay for a $20 purchase in a drug store. She later found out the issuer had decided to change the credit card account because of security concerns, but hadn't told her in advance. She had to wait a week for a replacement card. Today, the woman still hasn't seen her credit report and wonders whether it's safe to ask for it again. "Consumers should be alerted to the fraud and should be advised not to request credit reports from Equifax until the problem is resolved," she told On Your Side." |
| Story
About How Identity Theft Happened to one Victim |
Good
Advice
Roseman write "... if you're not receiving bills from credit granters as you normally would, find out what's happening. Fraud artists may call your credit card issuer and, pretending to be you, change the mailing address on your account and run up charges. Because your bills are being sent to the new address, you may not immediately realize there's a problem." permission to quote from the Toronto Star given by Ellen Roseman (writer) and Joanne MacDonald (TORSTAR SYNDICATE SALES) in emails in 2004. Copies of emails kept on file in the permissions binder. |
| This 2004 article by Ellen
Roseman, in the Toronto Star, outlines the main points for protecting yourself
from identity theft, including credit card theft.
While it is impossible to
prefectly protect yourself from all crime
Roseman's article contains some obvious points based on making sure bad guys, who are looking for personal information, will find it difficult to find information about you. |
| Protecting
yourself from Identity Theft
- be alert |
Roseman
suggests there are signs your identity is being used fraudulently:
1. You hear from a creditor
that a credit card application was received in your name and address. But
you didn't apply for it.
Roseman recommends "To prevent crooks from getting hold of data that lets them pretend to be you, you should pay attention to your billing cycles. Follow up with creditors when bills don't arrive on time." permission to quote from the Toronto Star given by Ellen Roseman (writer) and Joanne MacDonald (TORSTAR SYNDICATE SALES) in emails in 2004. Copies of emails kept on file in the permissions binder. |
Yau says "The article suggest that one of the best way to protect yourself from identity theft is to make it useless to thieves. You can try to do this by creating a profile which allows you to place on your credit files a notice telling prospective creditors to confirm with you by phone applications for new credit made in your name." |
In this article it discusses incidents of identity theft. It is difficult for law enforcemnt and government agenices to to "police" the internet, so it leaves victims with little or no options in recovering their identities. |
"I did some research on Identity Theft, an area that I was not familiar with and it's surprising to know that according to the article that 7-10 million people are affected per year by this kind of theft. This website provides information on the two types of identity theft "Account takeover" and "Application fraud",Coping with Identity Theft and Reducing the Risk of Fraud." There are about 30+ points on this page to guide you as to how to avoid being caught in an Identity theft situation. |
"Application fraud"
- is what some experts call
"true name fraud." The thief uses your identifying information to open
new accounts in your name.
The thing that makes Identity Theft problematic is that "Victims are not likely to learn of application fraud for some time, because the monthly account statements are mailed to an address used by the imposter. In contrast, victims learn of account takeover when they receive their monthly account statement."
Their web site www.privacyrights.org
says Copyright © 1995-2005. Privacy Rights Clearinghouse/UCAN.
This copyrighted document may be copied and distributed for nonprofit,
educational purposes only.
|
Tips on avoiding identity
theft
Reducing the Risk of Identity
Theft www.privacyrights.org/fs/fs17-it.htm#reduce
Reducing access to your
personal data:
1. To minimize the amount of information a thief can steal, do not carry extra credit cards, your Social Security card, birth certificate or passport in your wallet or purse, except when needed. At work, store your wallet in a safe place.
2. If possible, do not carry
other cards in your wallet that contain the Social Security number (SSN),
except on days when you need them.
.
| Protecting
your passwords
Protecting your passwords |
Improving password management
Microsoft explains "Creating stronger passwords can help protect you against identity theft. However, it does not guarantee that you are protected. In addition to the steps outlined here, review your monthly financial statements, and call the appropriate company or bank immediately to report issues. also, review your credit report each year. Together, these steps can help protect your identity—and your credit rating." |
from http://www.enquirer.com/editions/2002/01/11/loc_identity_thief_gets.html |
|
Identity theft from job
posting sites
| Identity theft can happen from a variety of sources - some of them not so obvious. Meghann V. in MRK 610 noted the recent case of Monster.com " acknowledging that some of its users are being targeted for identity theft via false job postings". When this story broke first week in March 2003 it was carried in a lot of online sites and offline newspapers. Meghann found reference to the story as it was carried on Internetnews.com and the basics are listed below. You should read this story because it is something that could happen to a student like you. (thanks Meghann) |
"One of the top Internet career sites, Monster.com, acknowledging that some of its users are being targeted for identity theft via false job postings, has issued a warning to millions of its registered users. " .
USA Today said "Pam Dixon, a research fellow with the Denver-based Privacy Foundation who has studied Internet job sites, said the e-mail confirms a growing hazard for online job seekers. "This is a very big problem and it's throughout the job search industry. It's not just on Monster. I've heard of this on all the major sites," she said." www.usatoday.com/tech/news/internetprivacy/2003-02-28-monster-warning_x.htm |
| KEY
POINTS |
Obviously Monster.com wants to publically address the news about potential identity theft on their site because they are at risk of the negative publicity effecting their business - if they suffer a steep decline in job seekers posting resumes, the company will be vulnerable in the competitive environment to job offerings being put on sites other than monster. |

Identity theft from job posting sites |
Monster dealt with the issue by "sent e-mails to job-seekers warning them about the possibility of attempts to steal personal information from fake employer job listings. The e-mail, called a "critical service message," reportedly says that "regrettably, from time to time, false job postings are listed online and used to illegally collect personal information from unsuspecting job seekers." |
| KEY
POINTS |
Some identity theft happens
not because an individual targets a vulnerable person, but because a thief
targets a source which allows access to hundreds or thousands of identities.
When such a theft is discovered there is obviously going to be a news story
break - which leaves the thief in a position of considering what action
to take:
|
| Story
About How a company's loss of data during a theft has created risk for Identity Theft in Canada
|
Sarah Schmidt,
National Post January 30, 2003
.. "Hundreds of thousands of Canadians are at risk of identify theft after a hard drive containing personal information was stolen from a leading data management company." "Social insurance numbers, pre-authorized banking information, dates of birth and pension details are stored on a hard drive stolen from a secure area of the Regina headquarters of Information Systems Management Canada, a subsidiary of IBM Canada. Among the ISM clients affected are Co-operators Life Insurance Co., which is based in Regina and provides protection for more than 500,000 Canadians, and several agencies of the Saskatchewan government.
In the case of ISM Schmidt reports "The Saskatchewan government has confirmed that personal records belonging to worker compensation board claimants and SaskTel and SaskPower customers are on the missing hard drive. |
.
|
|
CONTACT I MAIN PAGE I NEWS GALLERY I E-BIZ SHORTCUTS I INT'L BIZ SHORTCUTS I MKTG&BUSINESS SHORTCUTS I TEACHING SCHEDULE |
| . | |
|
MISTAKES
I TEXTS
USED I
IMAGES
I RANK
I DISCLAIMER
I STUDENT
CONTRIBUTORS I FORMER
STUDENTS I PUBLICATIONS
I |
|
| . |