CRACKING
& the Trojan Horse technique

| HACKING&
CRACKING & the Trojan Horse technique |
 |
see also http://www.witiger.com/ecommerce/hackersvideo.htm
 |
This web page has audio clips - just click on the icon (like the one to the left) and you can hear Prof. Richardson's voice adding additional information to topics on the page. |  |
turn on your speakers to hear audio clips |
| . | This page
used in the following courses taught by Prof. Richardson
.
|
| LEARNING
OBJECTIVES |
After completing
reading this unit, and listening to the lecture in class, students will
have information about:
o What
is Hacking
This page is prepared by Prof. Tim Richardson for his students. The purpose is to put some basic info together in one place about Hacking & Cracking. This is not intended to be an exhaustive treatment of the subject but rather a collection which would serve the purposes of students taught by "witiger". |
| INTRODUCTION | What is Hacking?
In the broadest terms hacking is just a slang expression for people that try to figure stuff out. For example, your microwave breaks down, so you buy a new one - but instead of throwing the old one out, you take it apart and look at the parts for interest sake to see if you can understand how it worked. In computer terms, hacking can be used in a mild way to describe simple looking for ways to see things - like hidden code on a page, or it can be used for strong meaning like a series of specific actions done to allow someone to access a password protected situation. One thing has to be clear to students, hacking requires curiosity, and knowledge - you have to have some degree of above average understanding of computers and the internet in order to do hacking things - otherwise you will not be successful; and, you must be curious - you must have a personality that causes you to want to find out how things work, or break them apart. It is this curiosity aspect that drives people do click around places on line and find out information that "normal" people wouldn't. If you were a person who, as a kid, liked to take apart the old family toaster, or if you ever unscrewed the back of an old SONY walkman to see how it works, you have a hacker personality. |
 |
YES THIS PAGE IS USEFUL
Nov 2011 - former UTSC student
(MGTD06
in 2008) Hasan Shahzad stopped by to talk about his work in Mutual Funds
at Royal Bank and mentioned that frequently he references material from
this page in order to educate clients as to some risk and threat situations
they should be careful about regarding identity theft and hacking.
Thanks Hasan for mentioning
this.
|
| What
is Hacking?
Definition |
Dave K. of MRK
610 in March 2003 found this site
formerly at http://www.hackerethic.org/hacker.html which has a good explanation of the several ways to think about hacking and what it means. "
this list comes from The Jargon File (published as The New Hacker's Dictionary [1996]), ed. by Eric Raymond |
|
pic submitted by Seneca MRK 616 student
|
Joeseph says
"I would like to touch onto the points you expressed about "Hacking." The term hacking seems to have a different perception between my generation and my parents generation. The word hacking to [my parents] instills fear and a sense of threat due to all of the negative press that has come with banking card fraud and identity theft through computer hacking. However I find with my generation we take the term hacking with less severity. I believe that this is do to the fact of how hacking has actually sort of helped us use popular gadgets like the iphone. When the iphone was first released Canadians were unable to use it because it would not work with our wireless carriers, however popular hacking programs like the "pwnage tool" developed by the dev team (a popular team of developers)http://blog.iphone-dev.org/ allowed for Canadians and people worldwide to purchase an Iphone that was not available yet in their country, and hack it themselves through a well developed and easy to follow " WTGR responds
|

pic submitted by Nick University of Toronto (UTM)
student NickB. sent an email March 2008 saying
Nick explains what happened to the right |
Nick says
I received a message from a friend on Microsoft Live Messenger that told me to open a file that was titled "pictures from last weekend". Considering i was with him that weekend i was tempted to open it. However, before i open any file sent to me on MSN, i ask the person what it is. There was no response from my friend so i discarded the message. About five minutes later i received another message from that same friend now saying "look how drunk i was" and there was another .zip file attached to it. I knew that something was wrong because this friend is never online on MSN and NEVER send me anything through it. I called me friend immediately and found out that he had opened a similar file on his computer and he now had a virus because of it. Because of the virus, his computer was now sending out corrupted virus files to everyone on his contact list. I found an article after class that explained how hackers where using this Trojan Horse virus, hidden in .zip files on MSN, to attempt to steal users' credentials by luring them on a phishing wesbite. After there login details wre stolen, the attackers could login into their accounts and find new victims by sending the virus link each of their contacts. The article also explained that because of the growing popularity of Instant Messenging, hackers are using it to send virusus in order to affect as many people as possible. After talking to my friends about the situation, i was surprised to find out that many of them have come into contact with this message previously from other friends they had on their contact lists and a good portion of them opened the file and now had a virus on the computer because of it. At the peak of this Trojan Horse virus i had approximately 6 .zip files a day from friends on my list who where wanting me to download files such as "look at Paris Hilton now", or "What was he thinking" Here is a link to the article,
|
..dfbd
| Trojan
Horse method of hacking |
.
dfbadb..dfbdbf
getcybersafe.gc.ca/cnt/rsks/cmmn-thrts-en.aspx Federal government list of threats |
| Trojan
Horse method of hacking |
Dr. Joseph Lo
wrote a good explanation of Trojan Horse attacks on the Internet Relay
Chat (IRC) Help website
http://www.irchelp.org/irchelp/security/trojan.html (link good in June 2016) These are a good list of
points to consider in terms of avoiding getting infected in the future?
Dr. Joseph Yuan-Chieh Lo is a professor at Duke University Medical Center |
| Trojan
Horse Defense |
1.NEVER
download blindly from people or sites which you aren't 100% sure about.
In other words, as the old saying goes, don't accept candy from strangers.
If you download commercial games or other software from "warez" sources,
you are not only breaking copyright laws, it's also just a matter of time
before you fall victim to a trojan.
2.Even if the file comes from a friend, you still must be sure what the file is before opening it (as Melissa and the "Love Bug" proved). Remember, just opening a trojan (by double clicking, previewing, etc.) unleashes its damage. In general, there is no reason for even a friend or colleague to send you an executable. When in doubt, ask them first, and scan the attachment with a fully updated anti-virus program. 3.Beware of hidden file extensions! Windows by default hides the last extension of a file, so that innocuous-looking "susie.jpg" might really be "susie.jpg.exe" - an executable trojan! To reduce the chances of being tricked, unhide those pesky extensions. 4.NEVER use features in your programs that automatically get or preview files. Those features may seem convenient, but they let anybody send you anything, not just dangerous trojans but also pornography, huge files to tie up your bandwidth and fill your disk, etc. For example, never turn on "auto DCC get" in mIRC, instead ALWAYS screen every single file you get manually. Likewise, disable the preview mode in Outlook and other mail programs. 5.Never blindly type commands that others tell you to type, or run pre-fabricated programs or scripts (not even popular ones). If you do so, you are potentially trusting a stranger with control over your computer, which can lead to trojan infection or other serious harm. 6.Don't be lulled into a false sense of security just because you run anti-virus programs, which do not protect perfectly against many viruses and trojans, even when fully up to date. Anti-virus programs should not be your front line of security, but instead they serve as a backup in case something evil sneaks onto your computer. 7.Finally, don't download an executable program just to "check it out" - if it's a trojan, the first time you run it, you're already infected! Dr. Joseph Yuan-Chieh Lo is a professor at Duke University Medical Center; he provided consent to use this list in an email May 19th, 2005. Copies of emails are kept on file in the permissions binder. |
www.theepochtimes.com |
During the 1st week of October 2007, Richardson was interviewed by Joan Delaney for the English-Canada version of the international newspaper The Epoch Times. The story was about Identity Theft and associated circumstances such as viruses, hacking and social engineering |
| Richardson was quoted saying "one of the reasons identity theft is on the rise is the ease with which intruders can hack into people's computers. "Think about guns for example; … can you imagine what would happen if you're walking down the street and guns are lying on a ditch and there's an arrow that says here's the bullets and there's another little arrow that says here's how to load it? Well, this is the problem with the Internet," says Richardson. "There are many websites where people can download simple hacking software and then use it to hack people, and then [there are] instructions in chat rooms and message boards about how to do hacking, and there is no law against that." " |
| Hacking
getting easier Hacking
|
"More
and more things are embedded in computers. We could put the same
code on a TiVo ( news - web sites) if we wanted to," Aaron Higbee, a security
consultant at Foundstone of Mission Viejo, California. TiVo allows people
to record TV programs while away or while watching other programs
at the same time. Firewalls -- the computer security barriers
that organizations depend on to defend against outside intrusions -- are
worthless against such attacks, Higbee said. While they are configured
to block suspicious traffic from getting into the network,
they also permit any type of traffic to get out, he said. To
create a tunnel to a remote computer, an attacker must first get physical
access to devices or network connections in the building. FIVE MINUTES
TO CREATE HAVOC Sometimes they can rely on unsuspecting souls inside
the company to do their dirty work for them by sending them an innocent-looking
compact disc that contains tunneling software. A disc containing
a special program to activate itself can find the network and reach
the Internet on its own, creating the opening for a hacker to wreak havoc
inside the company's network, Davis said. Another method of
unlocking the network door and opening the tunnel is for the hacker
to gain physical access to an office building and plug simple devices onto
the network. "Five minutes on the inside is all you need,"
said Davis, who does penetration testing for companies to
see how easy it is to compromise their systems. The speakers
demonstrated for the crowd how an attacker can slip a tunneling CD into
a CD-ROM drive, a Sega Dreamcast ( news - web sites) gaming console,
or a Compaq iPaq, and connect to the network. Once a connection is
established, devices such as the Sega game player can analyze the
network for routes data can travel to the Internet and establish a
secret tunnel to an outside computer controlled by the hacker."
Permission to quote from Yahoo!, use the Yahoo! logo, and use screen captures, was given in an email by Debbie Macleod, Yahoo! Marketing Manager Jan 21st, 2005. Copy of the email is kept in the permissions binder. |
| Hacking
consequences for business |
In this story, writtern by Peralte C. Paul of the The Atlanta Journal-Constitution, it was revealed that the company CardSystems Solutions, which handles credit card processing for VISA and AMEX had been badly hacked recently. Paul explains "The hacking incident, which CardSystems discovered in May, included 22 million Visa and 13.9 million MasterCard accounts. American Express and Discover have not provided numbers." As a result of so many accounts being comprimised, and investigation was launched by authorities. Paul writes "The company, which processed more than US$15 billion in transactions last year for Visa, MasterCard International, American Express and Discover Financial Services, already is at the center of two federal probes into its security breach." The story in July 2005 is that VISA and AMEX have decided to withdraw their use of services provided by CardSystems Solutions. A VISA spokesperson said ""Despite some remediation actions taken by the processor since the initial reporting of the data compromise, Visa cannot overlook the significant harm the data compromise and CardSystems' failure to maintain the required security protections has had on Visa member financial institutions and merchants, as well as the significant concerns it has raised for cardholders" Bottom line: if you get hacked, you can lose business; in the case of this American card processor, the business loss could be so large that it may force your company to close down. Permission to quote from ecommercetimes.com was given in an email by publisher Richard Kern in an email Dec 10th, 2004. Prof. Richardson is also a contributing writer to ecommercetimes.com. Copies of emails kept on file in the permissions binder. |
| Who
are hackers?
Mafiaboy |
The purpose
in talking about Mafiaboy is to give a window into how a person like this
came about, and the "impact on society" that his actions, and others like
him, had after his exploits where revealed.
In almost all cases of high level hacking (including mafiaboy) the cracker who carried out the actions boasts and brags about their actions to a circle of like-minded acquaintainces - this boasting is what inevitably gets them caught since someone usually then tells the authorities. The truly best "hacks" are never known cause people keep their mouth shut. The story of Mafiaboy has been carried on many online and offline magazines, newspapers - all over the world. One of the best summaries of the story, from a Canadian point of view, is the piece that appeared in the National Post in May 2002. Mafiaboy is a Canadian teenager from Montreal. |
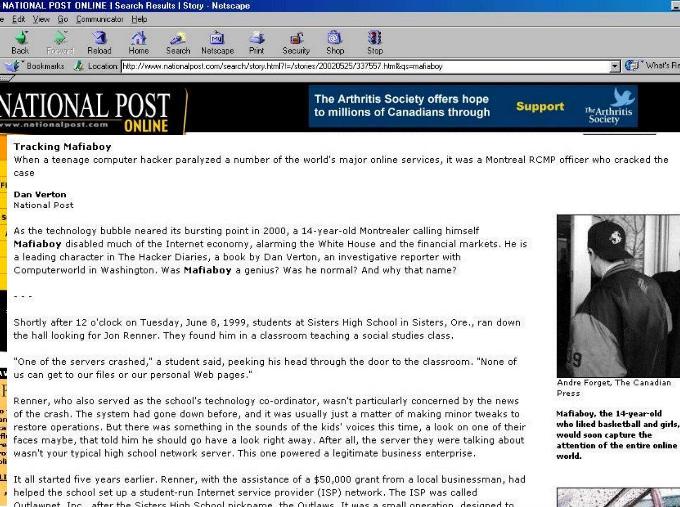
if you try to read this story
on the National Post site, and the link is taken down, click here
http://www.witiger.com/ecommerce/mfiaby.htm
| Gov'ts
involved in fighting hacking. |
.
 |
| Gov'ts
involved in fighting hacking. |
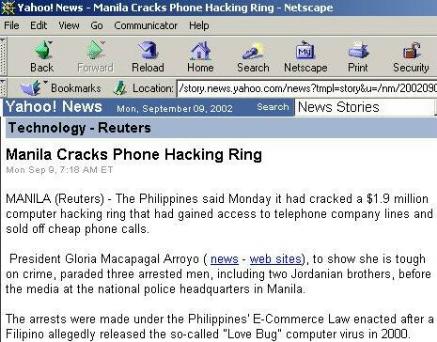
"The "Love Bug"
computer virus in 2000 caused damage estimated at $10 billion as it shut
down computer systems throughout the world, including at the Pentagon and
the British Parliament, but the Philippines had no computer crime law
under which it could make an arrest. The hacking ring was cracked after
the country's main phone company, Philippine Long Distance Telephone Co,
asked for help to stop the scam, police said. The hackers tapped into computers
controlling long-distance phone calls, then sold calls to their clients
at prices around half the normal rate. Immigration officials said two of
those arrested were Jordanians and the third was a Filipino. The
ring had amassed about $1.9 million from their hacking operations since
last year."
Permission to quote from Yahoo!, use the Yahoo! logo, and use screen captures, was given in an email by Debbie Macleod, Yahoo! Marketing Manager Jan 21st, 2005. Copy of the email is kept in the permissions binder |
| Pinging
|
Ping
- tests the connectivity between Internet hosts
|
| KEY
POINTS  |
The purpose
of showing you were such nasty stuff is on the WWW, is to prove a point
about the availability of programs which can be used to disrupt or bring
down sites.
If you therefore understand that there are many many places people can get such "tools", then you will be much more careful about your security online because you know that the threat and risk of an attack is very real. |
Hacking
tools are subdivided into some of these categories
|
| Hacking
- example of vulnerability to 3rd parties |
.
|
| Hacking
- Canadians at risk Hacking
|
.
|
| Hacking
- Canadians at risk
|
"The
Bank of Nova Scotia disclosed yesterday that 7,000 of its Visa customers
were exposed to the computer-security breach in the United States
that has left up to 8 million major credit-card accounts vulnerable to
fraud....It was the first such public statement to be made by a major Canadian
bank since the security breach, now determined to be a hacker attack,
was first reported late Tuesday night. About 3.4 million Visa accounts
and 2.2 million MasterCard accounts were affected, including 60,000 and
40,000 Canadian accounts, respectively. Both Visa International and MasterCard
International said in statement that they became aware in early February
that an "unauthorized intruder" had accessed the data, which was stored
by a third-party firm in the United States that processes transactions
for merchants."
permission to quote from the Toronto Star given by Ellen Roseman (writer) and Joanne MacDonald (TORSTAR SYNDICATE SALES) in emails in 2004. Copies of emails kept on file in the permissions binder. |
| Hacking
- College students getting into the campus computers |
.
"Christopher Andrew Phillips, who is studying computer science at the Austin campus, was charged with unlawful access to a protected computer and unlawful use of a means of identification. Phillips said he wrote and executed a computer program to access a university Web site that tracks employees who attend training classes, authorities said." Permission to quote from Yahoo!, use the Yahoo! logo, and use screen captures, was given in an email by Debbie Macleod, Yahoo! Marketing Manager Jan 21st, 2005. Copy of the email is kept in the permissions binder |
| Going
after the Hackers and Spammers
Bounties !
|
.
|
| KEY
POINTS |
There are mixed
opinions as to whether the offering of a bountry woud be successful with
spammers. It might work with Hackers and Crackers, who often brag about
their exploits in various online chats, and are therefore vulnerable to
a jealous person turning them in, but Spammers are motivated by money -
they don't brag about their exploits so much, and the successful ones make
enough money that they could counter-bribe people thinking about turning
them in.
A legal consideration would also be that anybody in a position to have enough inside information to turn in a Spammer, is probably someone who is themselves involved in illegal activity and may be vulnerable to prosecution. |
 |
click on the
screen capture to the left. It is a powerpoint presentation about hackers,
credit card fraud and identity theft.
The ppt. presentation is part of a "guest lecture" given by John Florinis. John is a Seneca BCS and IEC graduate and also a graduate of Ryerson University. At the time of the lecture March 2003 he was with the Internet Commerce section of Scotiabank. This dept in Scotiabank is responsible for Visa Account Information Security and has been recently [2003] sold to an American company www.paymentech.net |
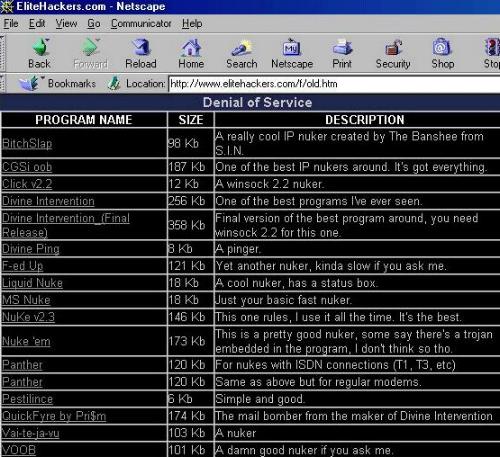 |
This is
one example of many places you can go on the Web to find programs that
you can download to do hacking and cracking. Some of the programs require
a considerable degree of hardware and software knowledge, some are just
"point and shoot"
One of the dangers of trying to download such programs is that the program itself may infect your computer with a result that compromises you seriously |
|
|
CONTACT I MAIN PAGE I NEWS GALLERY I E-BIZ SHORTCUTS I INT'L BIZ SHORTCUTS I MKTG&BUSINESS SHORTCUTS I TEACHING SCHEDULE |
| . | |
| MISTAKES ITEXTS USED I IMAGES I RANK IDISCLAIMER I STUDENT CONTRIBUTORS I FORMER STUDENTS I | |
| . |