


also
Bill C-6 aka PIPEDA
the
Personal Information Protection and Electronic Documents Act
also Bill C-37 the DO NOT CALL registry
also IPC www.ipc.on.ca office of the Information & Privacy Commissioner, Province of Ontario
see
also Privacy Issues re: Social Media www.witiger.com/ecommerce/privacyissues-social-media.htm
see
also Email Filtering www.witiger.com/ecommerce/emailfiltering.htm
 |
This web page has audio clips - just click on the icon (like the one to the left) and you can hear Prof. Richardson's voice adding additional information to topics on the page. |  |
turn on your speakers to hear audio clips |
| . | This page
used in the following courses taught by Prof. Richardson
.
|
 |
For
U of T students at the Mississauga Campus taking either CCT322 or MGD415
- be advised that Prof. Wensley covers Privacy Issues and the PIPEDA Act
(Cdn Bill C 6) in his course CCT 206.
In the case were students going through this unit are students who have previously taken CCT 206, we will not duplicate the topics you discussed with Dr. Wensley, rather we will touch on other aspects of Privacy Issues |
| LEARNING
OBJECTIVES |
After reading
this unit students will be able to:
|
| Why do we
care about privacy violations?
What does it matter if someone knows information about me? As Bruce Schneier points out in his book "Secrets & Lies: Digital Security in a Networked World" "Privacy violations can easily lead to fraud" Prof. Richardson explains that when criminally intent people have access to personal information about a target, they can combine sources of data to come up with a profile that will allow them to plan and attack people who are unprepared. Sometimes the risk may come from a person on the outside who has illegally obtained personal profile information for criminal purposes, or sometimes the risk may come from people within positions of trust.
Growing public awareness of these issues is one of the reasons why in Canada we have the new Bill C-6 federally and Bill 88 provincially. |
| Privacy
pressure for businesses to be more effective protecting customer profile information |
Gustavson notes: "businesses are facing a groundswell of pressure from consumers, governments and privacy advocates wanting to know how they collect, use and share a consumer's personal information in the marketplace." Gustavson explains: Two key developments are fuelling this:
|
| Privacy
pressure for businesses to be more effective protecting customer profile information |
"Protecting
privacy makes business sense"
consumer records lost or stolen Gustavson notes that in the U.S. "...more than 40 states have introduced data security breach laws" The consequence, for American
companies (and Canadian companies doing business in the U.S.) is "... a
patchwork of varying requirements that many marketers are struggling to
comply with." This adds a further burden to the job of "Chief Compliance
Officer" that is a title which has just become known since 2002.
|
| Privacy
pressure for businesses to be more effective protecting customer profile information |
consumer
records lost or stolen - employees fired
|
| Privacy
pressure for businesses to be more effective protecting customer profile information |
"Protecting
privacy makes business sense"
distrust and annoyance with some marketing practices Gustavson notes that "Contrary to some commonly held beliefs, legitimate businesses don't buy a consumer's personal secrets using covert means. Instead, they rent marketing lists of consumers who have either permitted the sharing of their personal information, or from demographically selected lists sourced from public information." but, adds WTGR, the circumstance that puts consumers in a vulnerable situation is when MEGA-databases take information from several lists (some acquired legally, some illegally) and combine this to create detailed personal profiles on customers - the problem being when these profiles are inaccurate, or give misleading information which may cause a customer to be denied credit, or pay a higher interest rate. Do Not Call Lists
|
DO
NOT CALL lists

(part of Astral Media) |
During
the 3rd week of September 2008 Richardson was interviewed, live on air,
by host Jim Richards on CFRB newstalk 1010 for a short segment on the upcoming
"Do Not Call List". Richardson
answered questions live on air, the segment can be heard by clicking on
the link below
http://people.senecac.on.ca/tim.richardson/audio/CFRB2008Sept22DoNotCallList.mp3 (link works 2014) |
| Privacy
DO NOT CALL lists Bill C-37 |
"Protecting
privacy makes business sense"
distrust and annoyance with some marketing practices Bill C-37 (became
law in 2005)
Read 2005 article by Prof.
Michael Geist
"Bill C-37 introduced Canada's
proposed do-not-call legislation in December 2004. Amending the Telecommunications
Act, the proposed legislation would allow the CRTC to establish a national
bilingual do-not-call list to which individuals not wishing to receive
unsolicited calls could add their telephone numbers. Telemarketers who
call individuals on the national registry will be committing an offence
and subject to monetary fines."
|

| Privacy
DO NOT CALL lists Ways to Annoy a Telemarketer |
10 Ways to Annoy a Telemarketer 10. When they ask "How are
you today?" Tell them! "I'm so glad you asked
8. Cry out in surprise, "Judy!
Is that you? Oh my God! Judy, how have you been?"
7. If MCI calls trying to
get you to sign up for the Family and Friends Plan,
6. If they want to loan you
money, tell them you just filed for bankruptcy and
5. Tell the telemarketer
you are on "home incarceration" and ask if they could
4. After the telemarketer
gives their spiel, ask him/her to marry you. When
3. Tell the telemarketer
you are busy at the moment and ask them if they will
2. Insist that the caller
is really your buddy Leon, playing a joke. "Come on
And first and foremost: 1. Tell them to talk VERY
SLOWLY, because you want to write EVERY WORD down.
|
|
advanced technologies revealing privacy vulnerabilities |
The basics of the story is, as Paul outlined in the first sentance "Social networking sites
and advances in mobile technology are giving advertisers an unprecedented
ability to focus their pitch to a very specific focus group: you."
the full article was at www.cbc.ca/news/background/tech/hightech/personalized-ads.html |
|
advanced technologies revealing privacy vulnerabilities |
Weeks' story, carried in
the National Post,
states that
Weeks' says that "... the program, which relies on pictures taken without the knowledge or consent of people in them, seems to violate many basic rights of citizens and poses a serious threat to personal privacy." according to Jennifer Stoddart, Canada's Privacy Commissioner. |
|
advanced technologies revealing privacy vulnerabilities |
Weeks points out "the privacy commissioner is concerned that if the service is expanded into Canada, it could violate [Canadian] federal privacy laws designed to protect citizens from having their personal information easily accessible. The street-view application "does not appear to meet the basic requirements of knowledge, consent, and limited collection and use" of personal information that is set out in Canada's privacy laws, the commissioner wrote in her letter to Google's chief legal officer David Drummond. " |
|
advanced technologies revealing privacy vulnerabilities |
Google's
detailed streetscapes raise privacy concerns
"Here is a link I came across, reminded me of different ways people are using the current technology and also the rights these new technologies may be infringing on. It is an apparent drug deal caught by the street view cam in Google maps." http://maps.google.com/maps?hl=en&ie=UTF8&layer=c&cbll=41.823471, -87.612699&cbp=1,167.75819312895956,0,3,12.173258141222098&ll=41. 837915,-87.609787&spn=0.047193,0.066605&t=k&z=14 Below is a screen capture you can view if the Google link is no longer active 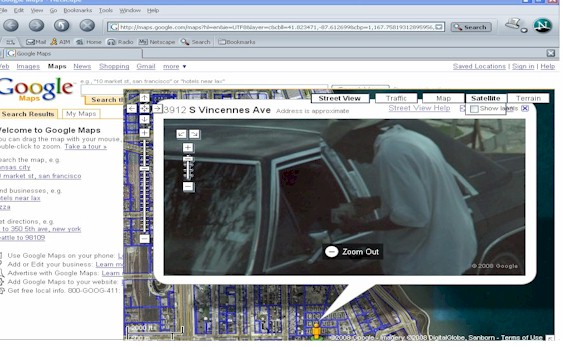 |
| Privacy
new
|
Arellano explains that "Ontario's Information and Privacy Commissioner has expressed support for Microsoft's user identification system dubbed CardSpace Identity Selector. Microsoft Corp. plans to launch CardSpace as a Windows component embedded in the company's Vista operating system (OS) expected to roll out in January [2007].
see also http://cardspace.netfx3.com/content/introduction.aspx |
| Privacy
new
|
Arellano writes
that "Microsoft executives .... described CardSpace as an identity metasystem
that allows a user to create multiple virtual ID cards. ...each virtual
card created by the user will only contain the minimum amount of information
that individual will need to divulge to carry out a transaction applicable
to the card. "The system allows users to create a palette of cards. Users
can choose which card they want to use depending on the context of the
transaction to be carried out. For instance, if a CardSpace user wants
to buy something from an online store, he or she can use a virtual card
tagged for credit card purchases. The cards do not contain any data such
as social insurance numbers or credit card information that could be used
for Internet fraud. The virtual card will connect the online store to a
bank's system that will vouch for the user's identity and inform the store
if enough funds are available for the purchase."
full text of the article is at witiger.com/ecommerce/articleIDcard.htm |
 |
In
November of 2005 one of the most startling things to be discussed in the
Canadian media was the stunt pulled by Maclean's magazine when they wrote
a story about Privacy Issues and showed how they could obtain the personal
cellphone call records of the Privacy Commissioner.
As expected, this resulted in a lot of inquiries from the Privacy Commissioners office about how the average citizen was vulnerable to people being able to obtain personal and private information. In the case exposed here, journalists for Maclean's had bought the cell phone records from a large American media company that sells all kinds of information over the internet, as long as the buyer wants to pay the fee. WTGR |
| Federal
Privacy Commissioner Exposed |
Jonathon Gatehouse
of Maclean's writes
"When police are investigating a crime and want phone records, they must seek a court order. Most Canadians consider their call records privileged information, and the courts have backed them up time and time again. Yet Maclean's was able to purchase the privacy commissioner's phone logs online from a U.S. data broker, no questions asked. For about US$200 per order, Locatecell.com delivered months of long-distance records from her Bell Canada home and cottage accounts. They were also able to access her Telus Mobility cellphone call logs for October -- a monthly bill she probably hadn't even received at the time. And all the Internet requests were turned around in a matter of hours." says Gatehouse Gatehouse adds "...in the wired world, almost anything is available for a price. A British teen recently tracked down his sperm-donor father using his own DNA and two different for-hire databases." |
| Privacy
Commissioner Exposed  |
The circumstance
of a U.S. company, collecting personal profile information throughout North
America, raises the question of how "sovereign" our country can be when
rules, laws and regulations passed by the Canadian federal and provincial
governments have no limitation on a person who uses non-Canadian resources
to access information.
Truly this is one of the consequences of the Information Age eliminating political boundaries whether we like it or not. |
| How to find that private info | UTM student
James B. in MGD415 in January 2006 searched some info related to the story
and sent an email - some of which is included below.
Prof. Richardson, I was reading the competitor intelligence portion of your website tonight, which reminded me of a news article I saw the other day. It was about companies on the internet that for a fee, will provide you with a complete record of a person's cell calls; including out going/incoming number, date, time, etc. I did a bit of research, and checked out one of these sites (http://www.datatraceusa.com/products.asp, I know it's American, but I believe they will still search Canadian numbers), and they actually have services where if you know person's name & address, they can provide you with their cellphone number, or if you simply know a cell number, they can provide you with the name and address of the owner. I'm not sure if this would qualify under 'competitor intelligence or a 'security/privacy' section. This Chicago Sun Time's article looks at how this service is putting government/police informants at risk. I think that this service has the ability to be used to gather competitor intelligence if a company knew the name of several important employees at a competing company, where using their names could find out their cell phone numbers, and therefore find out the major numbers they are calling and other detailed information. This information could give the company an idea to possible suppliers, buyers, financiers, etc. Hope this information is relevant, and helps. BTW, here is the original Chicago Sun Times article: http://www.suntimes.com/output/news/cst-nws-privacy05.html |
| Enforcement
Issues |
As journalist Jonathon Gatehouse wrote in the Maclean's exposure of the Privacy Commissioner, "The Canadian Radio-television and Telecommunications Commission, which regulates telecom companies, has a little more power to punish privacy breaches -- its rulings have the force of law. But the maximum fine for a corporation's first offence is $50,000 -- not much of a deterrent when you consider the multi-million-dollar penalties handed down by its American counterpart, the Federal Communications Commission. On very rare occasions, Canadian police will get involved in a privacy issue, but only if the breach results in a serious crime -- like the 2002 case of the Quebec government employee accused of helping the Bandidos motorcycle gang plan hits by providing them with the driver's licenses of rival Hells Angels." |
| Bill
C-6
PIPEDA Privacy
Bill C-6
|
titled "Privacy law will affect e-commerce" Roseman's piece was about the effect of Bill C6 passing in 2000. Bill C6 is federal legislation. The legislation "requires Canadian companies and institutions to get informed consent before they collect or disclose personal information". Since so much of internet marketing is focused at target marketing - which is facilitated by gathering databanks of personal demographic information about on-line consumers, this legislated requirement will be a big topic in "e-commerce legal issues". permission to quote Roseman given by Joanne MacDonald, TORSTAR Syndicate Sales, in an email 2004 Dec 09 |
| KEY
POINTS  |
Privacy Issues
have to be dealt with effectively.
Privacy concerns remain one of the principal reasons consumers hesitate to purchase products through the web. One of the reasons the Canadian law (Bill C6) was enacted was due to pressure from the public, and then politicians, to address the situations of abuse created when private companies buy personal data information collected by government departments and agencies - and then get caught using that information in ways which can be considered harmful to the identities of the people listed. Unfortunately, the law only applied to Canadians and Canadian companies and is not enforceable outside Canada. |
| Bill
C-6
Privacy
Bill C-6
|
Bill C6 [2001] requires
companies that collect and use personal information about customers, to
comply with new regulations to safeguard what they can do with that information.
permission to quote from Computing Canada given by publisher Joe Tersigni of itbusiness.ca, the parent company, in May 2005. Copies of emails kept on file in the permissions binder |
| Bill
C6
Basics |
"Electronic Documents Act (PIPEDA). (informally referred to as Bill C6) The PIPEDA establishes new rules to recognize the privacy rights of individuals with respect to the collection, use, disclosure and retention of their personal information. The rules also recognize the obligations of organizations to protect personal information in a manner that a "reasonable" person would consider appropriate under the circumstances. To comply with the PIPEDA requirements, businesses must implement a privacy compliance regime. The federal government is phasing in the legislation to ease the transition for businesses and to give provincial governments an opportunity to come up with their own privacy legislation. By January 1, 2004, the privacy rights of all Canadians will be protected in one of two ways: by federal legislation or by provincial legislation that is "substantially similar" to the federal legislation. Those rights are to be enforced by the Privacy Commissioner of Canada who receives complaints about contraventions of the rules, conducts investigations and attempts to resolve such complaints. Unresolved disputes can be taken to the federal court for resolution and this may result in fines of up to $100,000. " |
 |
During the 2nd week of January 2007, Richardson was interviewed by InterGovWorld.com for a story about Bill C6, (the PIPEDA Act) regarding new lesgislation about security breach notifications |
| PIPEDA is currently [2007Jan] under review by the House of Commons Standing Committee on Access to Information, Privacy and Ethics. Richardson was quoted in the context of security breach notification requirements saying "This proposal is extremely important, otherwise PIPEDA would have no teeth,""The question now is, how will the law be enforced? "Richardson points out that it's yet unclear which agency would enforce the proposed law and how its enforcement would be handled. |
| when
a
third party gets a hold of your personal information
|
Goar says "Anyone who uses
a computer, owns a credit card, subscribes to a magazine or donates
to charity is in dozens of privately owned databases. Anyone who
applies for a passport, casts a ballot or visits a doctor is in government
databases that may or may not be secure; may or may not be publicly managed;
and may or may not be accessible to the police."
"Bill C-17, which is now
[Feb 2003] before Parliament. It would give the RCMP and CSIS the
right to delve into the background of anyone booked on a domestic
or foreign flight."
|
| Privacy
Commissioner Ontario
|
the Ontario Privacy
Commissioner www.ipc.on.ca
As explained in their own words "The role of the Information and Privacy Commissioner/Ontario (IPC) is set out in three statutes:
www.e-laws.gov.on.ca/html/statutes/english/elaws_statutes_90f31_e.htm www.e-laws.gov.on.ca/html/statutes/english/elaws_statutes_90m56_e.htm www.health.gov.on.ca/english/public/legislation/bill_31/priv_legislation.html www.health.gov.on.ca/english/public/legislation/bill_31/personal_info.html www.health.gov.on.ca/english/providers/legislation/priv_legislation/quality_info.html |
| Privacy
Commissioner Ontario
|
from the website of the
Ontario Privacy Commissioner Sept 2007
|
| Protecting
Your Online Privacy |
EFF's Top 12 Ways to Protect Your Online Privacy Jo C. in BCS 555, Nov 2003, found this helpful list of 12 Ways to Protect Your Online Privacy. Some of the entries on the list are obvious, some are worth remembering. the detailed list came from www.eff.org/Privacy/eff_privacy_top_12.html (link not working in 2013)
|
| Privacy
Issues Globally
|
"Private email is not always Hush Hush" Professor Geist explains that sometimes U.S. government agencies have the power to use certain regulations and legal circumstances that result in Canadians having their expecation of privacy nulified. Geist explains that "This past September [2007], the U.S. Drug Enforcement Agency launched "Operation Raw Deal", an initiative that targeted people purchasing raw steroid materials through the Internet from China and repackaging the steroids as drugs for domestic sale." "The foundation of the DEA's case rested on hundreds of encrypted emails stored on the computer servers of Hush Communications, a company based in Vancouver. A British Columbia court ordered the company to decrypt the emails and to send them to the U.S. law enforcement officials....the company complied, shipping 12 CDs filled with unencrypted personal email to investigators in California." U.S. officials relied on the U.S.-Canada Mutual Legal Assistance Treaty, which is used by law enforcement agencies to expedite investigations that run across national borders. Geist cautions "the use of
the MLAT serves as a timely reminder that U.S. law enforcement wields a
wide range of investigative tools to compel disclosure of private information
held in Canada."
As explained in the Toronto Star "Hush Communications www.hushmail.comis a free encrypted email service that allows users to blanket their electronic communications with privacy-protective encryption."
permission to quote given by Prof. Michael Geist in a May 2005 email, copies on file in the permissions binder see also michaelgeist.ca |
| Privacy
Issues Globally Privacy
|
"Tighter surveillance
worries privacy groups"
"WASHINGTON — Governments worldwide have made it easier for authorities to augment citizen databases and eavesdrop on telephone and online conversations in order to fight terror, according to a survey of privacy regulations. The report, written by privacy activists Electronic Privacy Information Center www.epic.org and Privacy International, show the United States was not alone in passing new laws that value increased security over personal privacy. permission to quote given by Joanne MacDonald, TORSTAR Syndicate Sales, in an email 2004 Dec 09 |
| Privacy
Issues Globally Privacy
|
Here
is the web page for the actual Report noted in the 2002 Star article
http://www.privacyinternational.org/survey/phr2002/ "It's
a general theme toward total identification," said Sarah Andrews, an author
of the report, which was released last week. "When you're outside in public
or when you're online, you can be identified.'That dismays privacy groups,
which worry about free speech restrictions and abuses of power. They
have fought new laws like the U.S. anti-terror legislation
that lowered the bar on surveillance requirements by authorities.
"Stewart Baker, a former general counsel for the NSA, said increased data sharing might have helped identify the Sept. 11 hijackers. He said many surveillance proposals were already moving toward passage, and speeded up by legitimized fears of a terrorist threat. "They're really complaining about changes in the world rather than changes in the law," said Baker. |
| Privacy
Issues 5
|
Barshack explains that "for e-businesses that want to sell successfully online and instill trust in their customers, privacy is not always a black and white matter. The shades of gray inherent in the privacy debate are many, which is why different approaches to Web privacy can be appropriate and important for different types of consumers and the online businesses that serve them." |
| Privacy
Issues 5
|
Barshack: "five
things that e-businesses need to think about when tackling the big "P."
1. "Privacy means different things to different audiences". In B2B companies accept that the seller keep s as much detailed information about the customer as possible to facilitate reordering. In B2C customers think detailed information on their previous product purchases and demographic information about them is an infringement and can be abused if the information is sharedpermission to quote from ecommercetimes.com given by publisher Richard Kern in an email Dec 10th, 2004. Prof. Richardson is also a contributing writer to ecommercetimes.com. Copies of emails kept on file in the permissions binder. |
| Privacy
Issues 5
|
2. "Honesty
is always the best policy, period."
"Companies need to clearly and conspicuously disclose their privacy policies." says Barshack |
| Privacy
Issues 5
|
3. "Show
your Web visitors that knowledge and a better understanding of them
can work in their favor."
You can be more successful at asking for, and receiving detailed information on customers' interests if you can prove to them it is an advantage to do so - either saving money or more accurate product selection. |
| Privacy
Issues 5
|
4. "Separate
business from the personal without sacrificing personalization."
"There's a big difference between understanding buying patterns on a business-to-business or business-to-consumer commerce site for the purpose of improving the site and the visitor's experience (i.e. personalization) on the one hand, versus following Web surfers into chat rooms and through Internet activities completely unrelated to their commercial interests." |
| Privacy
Issues 5
|
5. "The
flip side of privacy: It's a two-way street."
"E-businesses have privacy concerns, just as consumers do. Especially with B2B sites, companies are often opening up their entire enterprise to the public, a potentially vulnerable situation...Show your customers that you are serious about protecting their information, just as you are serious about protecting your own" |
| Privacy
Issues Corporate Considerations |
|
| Privacy
Issues examples
|
"Details of the study and JetBlue's involvement were reported Thursday 2003 Sept 18, by Wired.com, which credited privacy activist Bill Scannell for bringing attention to the issue on his Web site, Don't Spy On.Us. Marc Rotenberg, executive director of the Electronic Privacy Information Center in Washington, said that by violating its privacy policy, JetBlue could be sued for "deceptive trade practices." " Permission to quote from Yahoo!, use the Yahoo! logo, and use screen captures, was given in an email by Debbie Macleod, Yahoo! Marketing Manager Jan 21st, 2005. Copy of the email is kept in the permissions binder. |
| Privacy
Issues Technology
|
.
"Privacy on the Internet" by Penney Kome, originally at www.womenspace.ca/magazine/51ws/vol51f.html Kome explains "In November 1999, RealNetworks acknowledged that its Real Jukebox software secretly gathered and transmitted data about consumer listening habits. If Sally Jones listened to the new Sarah McLaughlan song thirty-six times in a row, RealNetworks knew." "The free version of RealJukebox,
which has about 13.5 million registered users, prompts new users for their
names and e-mail addresses before they are assigned an identifying number,"
according to an E-Commerce Times story by Mary Hillebrand on November
9, 1999.
|
| Privacy
Issues Technology
|
.
Hiawatha Bray of the Boston Globe wrote a story published online November 8th, 2005 titled "Sony CDs secretly install spyware" Bray wrote "Computer Associates International Inc. said that new anticopying software Sony is using to discourage pirating of its music also secretly collects information from any computer that plays the discs. The software works only on computers running Microsoft Corp.'s Windows operating system. It limits listeners' ability to copy the music onto their computers, and locks copied files so they cannot be freely distributed over the Internet. But Computer Associates said the antipirating software also secretly communicates with Sony over the Internet when listeners play the discs on computers that have an Internet connection. The software uses this connection to transmit the name of the CD being played to an office of Sony's music division in Cary, N.C. The software also transmits the IP address of the listener's computer..." |
| Global
Positioning System
-Privacy Issue  |
How that information will be used has raised some privacy advocate eyebrows. Will the users of these location-based games know what they're getting into?" |
 |
This website www.wirelessweek.com
is about privacy issues regarding GPS-based games, which are popular in
some countries.
"In many countries around
the world, a GPS-based game called "geocaching" is growing in popularity.
As precise location capabilities become part of wireless networks, these
kinds of
|
| Marketing
Opportunity Vs Privacy Issues
|
Mobile Commerce
Privacy Issues
The following information was originally taken from: www-2.cs.cmu.edu/~sadeh/mobilecomm.htm ISRI - School of Computer Science - Carnegie Mellon University
"As the Internet finds its way into our purses or shirt pockets, the devices we use to access it are becoming more personal too. Already today, mobile phones and PDAs know the phone numbers of our friends and colleagues. They are starting to track our location. Tomorrow, they will replace our wallets and credit cards. One day, they may very well turn into intelligent assistants capable of anticipating many of our wishes and needs, such as automatically arranging for taxis to come and pick us up after business meetings or providing us with summaries of relevant news and messages left by colleagues. But, for all these changes to happen, key issues of interoperability, usability, security, and privacy still need to be addressed. " permission to link and quote
was given by Prof. Norman M. Sadeh, Director, Mobile Commerce Lab.
|
..
.
|
|
CONTACT I MAIN PAGE I NEWS GALLERY I E-BIZ SHORTCUTS I INT'L BIZ SHORTCUTS I MKTG&BUSINESS SHORTCUTS I TEACHING SCHEDULE |
| . | |
|
MISTAKES
I TEXTS
USED I
IMAGES
I RANK
I DISCLAIMER
I STUDENT
CONTRIBUTORS I FORMER
STUDENTS I PUBLICATIONS
I TIPS
I |
|
| . |