
Chpt 4
Chpt 5
| SECTION 1 ©
Chpt 4 E-commerce and the role of Third Parties Verisign, TRUSTe Chpt 5 The
Regulatory Environment
Copyright on the WWW
Privacy Issues in Canada, Bill C6 web linking; domain name disputes
|
changes last made to this page 2006 May 16
In Section One we will use material
from the following texts
 |
2nd Edition
Chpt 4 Chpt 5 |
course author:Tim Richardson
| . | Learning Objectives
for Section 1
Section 1 is organized such that after completing this section participants will be able to
|

Chpt 4 E-commerce and the role of Third Parties |
|

Chpt 4 E-commerce and the role of Third Parties  |
Chpt 4, page 125
"Web sites displaying the TRUSTe Privacy Seal are committed to abiding by a privacy policy that gives users notice, choice, access, security, and redress with regard to their personal information."
Under the heading of education, TRUSTe has a section titled TRUSTe's Privacy Protection Guidelines - go there www.truste.com/education/protection_guidelines.html they have 6 points 1. Read Privacy Statements. |

Chpt 4 E-commerce and the role of Third Parties  |
Chpt 4, page 126
"Specifically, Veri-Sign provides products that allow websites to transmit encrypted data and to provide authentication about the source and destination of the data"  www.verisign.com/corporate/about/index.html
www.verisign.com/corporate/about/index.html
.
Network Solutions used to be the original Domain Name registrar. VeriSign bought Network Solutions and through its acquisition of Network Solutions, VeriSign is the world leader in domain name registration. |

Chpt 5 Regulatory Environment
|
"Regulation of Electronic
Commerce and the Internet is slowly Evolving" - the lead in sentance to
Chpt 5
Each Country has three categories of Internet Users to serve:
|
| Cryptography
Issues 
Chpt 5 Regulatory Environment |
Regulatory Environment,
Cryptography Issues
2nd ed. page 146 Export of Cryptographic Products
|

Chpt 5 Regulatory Environment
|
Regulatory Environment
2nd ed. page 156 Third-Party Sharing / Selling of Data
|

Chpt 5 Regulatory Environment
|
Regulatory Environment
2nd ed. page 157 Carnivore
|
META Tags

Chpt 5 Web Linking Issues META Tags
|
Web Linking Issues
2nd ed. page 160 Linking Using Trademarks in Keyword META Tags
|

Chpt 5 Web Linking Issues
|
Web Linking Issues
Linking to Illegal Files 2nd ed. page 161 "Unfortunately the ease of scanning images
and [copying] digital recordings of music and video make it easy for "bootlegged"
copies of music and pictures to reside on the Internet. ...MP3 is one such
compression technology thathas made it feasible to upload and download
digital audio files that were otherwise to large to transmit"
|
 |
screen capture leading to a special section on registration issues of Domain Names |
 |
screen capture leading to a special section on marketing issues of Domain Names |

Chpt 5 The Regulatory Environment |
Domain Name
Disputes
Citing our military role as international peacekeepers, a story in ComputerWorld Canada in May, 2000 noted a Montreal company, named eResolution, backed by ICANN (Internet Corporation for Assignment Names and Numbers), is in a position to handle the full adversarial proceedings from initial complaint filing to the arbitration stage and transfer of evidence. |
| Domain
Name Hijacking 
Chpt 5 The Regulatory Environment Domain
|
"The low cost and ease of domain name registration has allowed individuals to register domain names of well-known companies. The intent by many registrants was to hold these domain names hostage until a company would offer to buy the rights to use the domain name"
The text says on page 165 "Registrations are approved on the basis of the assumption that no other entity has a legal right, such as a registered trademark, to use that domain name. If that assumption proves false, ICANN reserves the right to reexamine the registration of that domain name and generally gives preference to entities with a federally registered trademark." |

Chpt 5 The Regulatory Environment |
Privacy Issues
2nd ed. page 149
|
 |
screen capture leading to a special section on Privacy Issues |
.
.In Section Two we will use material
from the following texts
 |
1st Edition
Chpt 5 |
 |
2nd Edition
Chpt 7 |
|
 |
Chpt 2
Chpt 3 Chpt 4 |
 |
Chpt 1
Chpt 2 |
|
 |
Chpt 2 |
course author:Tim Richardson
| . | Learning
Objectives for Section 2
Section 2 is organized such that after completing this section participants will be able to
|
| Chpt 5
1st Edition 
Chpt 7
Chpt 5
Chpt 7
Chpt 5
Chpt 7
|
"Electronic Commerce":
Greenstein & Feinman, (1st Edition) Chpt 5 The Risks of Insecure Systems Greenstein & Vasarhelyi, (2nd Edition) Chpt 7 The Risks of Insecure Systems the powerpoints for Chpt
5 (1st Ed) can be obtained from
Page 215 Greenstein Text - 2nd Edition "Until recently, most information security breaches were initiated by insiders. However a study by the CSI Computer Security Institute and FBI indicates that this trend is rapidly changing. The findings indicate that the number of external attacks is growing because if the increased use of the Internet" Overview of Risks Associated with Internet Transactions
risks associated with transactions between business partners risks associated with confidentially-maintained archival, master file and reference data risks associated with viruses and malicious code overflows (in addition to the information in the Greenstein text, scroll down to viruses) buffer overflows |
 |
screen capture leading to a special section on witiger.com about DNS Attacks |
 |
screen capture leading to a special section on witiger.com about cookies |

Chpt 3 Types of
Types of
|
Secrets &
Lies: Digital Security in a Networked World
by Bruce Schneier Chpt 3 Attacks
|

|
Principles
of Information Security
by Michael Whitman and Herbert Mattord Chpt 2 The Need for Security
A summary of the Threats described in Chpt 2 is listed below Five groups of "real and present" danger
|
 |
Principles
of Information Security
by Michael Whitman and Herbert Mattord Chpt 2 The Need for Security
|

Chpt 3 Types of
- Frauds |
|

Chpt 3 Types of
- Scams |
Scams
Schneier quotes the National Consumers League (Chpt 3, page 24) "the five most common online scams are
|
 |
Privacy Violations
In many countries, people do not own the information which is collected about them, that is to say, their personal data. This information is considered the property of whatever credit card company, insurance firm, educational institution that collected the information. As a consequence of some outrageous violations of collecting and disseminating personal information, Canada, New Zealand and other countries have enacted tough laws which are binding on the companies that collect and pass on personal profile information (which we noted in Section 1 of this course when we presented the federal and provincial legislation dealing with this). Privacy violations are not, strictly speaking, criminal activity, but, depending on what is done with the information, it can be used for criminal purposes - such as assuming an identity for the purposes of obtaining credit, which could then be used to fraudulently buy products and services. As a person studying IT security, it would be your responsibility to understand that protecting the private personal information of people that have data held within your firm's IT systems, is critical to conduct effectively and without risk. |

Chpt 3 Types of
- Privacy Violations |
Privacy Violations
Schneier, page 29
If the attacker wants to know everything about
As Schneier says, "this attack harnesses the power of correlation" Data harvesting is only worthwhile
doing if it can be automated, and computers allow the automation process
to be done very effectively. Using good cryptography will thwart harvesters
since they will not be easily able to identify if what they are looking
for is in the target they are attacking.
|

Chpt 3 Types of
Types of
|
Secrets
& Lies: Digital Security in a Networked World
by Bruce Schneier Chpt 3 Attacks
Schneier gives an amusing example noting that in the hours leading up to the 1991 bombing of Iraq, pizza deliveries to the Pentagon increased one hundredfold - even if you did not know what the generals and admirals were talking about, it had to be something important from which there would be some serious time spent on decision making.
|
| Internal
Threats |
Internal
Threats
|
| Internal
Threats |
.
" A firewall is not enough. Proper network security requires at least one (if not several) firewalls, anti-virus software and intrusion detection. That's just the technology, which is not even the most important part. Security also depends on policies and procedures, and without those, all the gadgets in the world will not be enough... external threats are just a small part of the security picture.... threats from outside have increased in the last couple of years, but insiders still pose a more serious risk than outsiders" Threats come from
|
| Internal
Threats |
|
| Handling
Internal Threats |
.
Handling Internal Threats by initiating policies and procedures to cut down on risk situations developing. "Deloitte
Consulting LLC prohibits employees from storing documents from work
on their home computers, says Karim Zerhouni, head of the consulting firm's
Canadian internetworking practice. That policy makes it less likely confidential
information will fall into the wrong hands. Yet policies and
procedures are not the complete answer either. Hardware and software can
help enforce the rules and make it easier for employees to comply with
them. Access controls and passwords can be used to limit employees'
access to the applications and data they need to do their jobs and
keep them away from privileged material. Authentication technology
can ensure that e-mails come from whom they appear to come from and
that documents have not been tampered with."
|
| Internal
Threats |
Internal
Threats, Logic Bombs
|
 |
The disgruntled
employee poses but one of many insider threats to information systems
and the valuable data stored therein. Unauthorised access from insiders,
rather than outside hackers, accounted for 44% of network security breaches
last year, according to the March 2000 survey by Computer Security Institute
(CSI) and the FBI.
"The greatest exposure to any organisation is what I call the knowledgeable insider - anybody from a janitor to a vendor or an active or ex-employee," says Steve Dougherty, director of information security at the Fulsom, California-based California Independent System Operator, which is taking over management of power grid transmissions for 27m Californians with the state’s recent industry deregulation. American Society for Industrial Security’s (ASIS). 89% of respondents to the ASIS 1997/1998 Intellectual Property Loss Special Report indicated that their biggest concern regarding system security is retaliation from disgruntled employees.. |
| University
College computers - a weak link |
|
| Risks
With Business Partners they
may
Risks
they
may
|
Microsoft - which one would presume is very very careful about who they partner with, is often vulnerable when the partner makes a bad mistake. Some of these mistakes happen when the intermediary is responsible for dispensing some service, such as making downloads available. In the screen capture below, you can see Prof. Richardson has received an email from SANS. This email details how Microsoft Hotfixes downloaded from the Premier Support and Gold Certified Partner web sites were infected with the Fun Love virus. 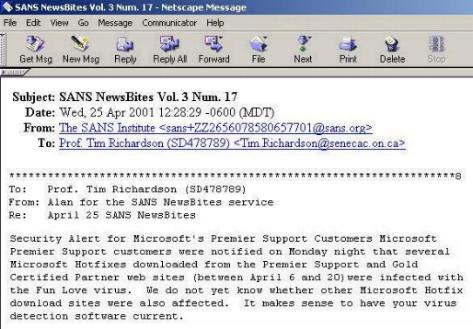 The original email has been
uploaded to the ECP site and you can read the full text, including other
warnings and info at
|
| Risks
With Business Partners Hacking
Risks
Hacking
|
.
|
 |
screen capture leading to a section on witiger.com about Viruses |
..
 Printers
vulnerable? - sure. Printers
vulnerable? - sure. |
NATIONAL
INFRASTRUCTURE PROTECTION CENTER (United States) - noted page 214 in Greenstein Text - 2nd Ed. |
| NATIONAL INFRASTRUCTURE
PROTECTION CENTER
"Intrusion Techniques: Networked printers are prime targets for denial of service attacks and root access intrusion attempts 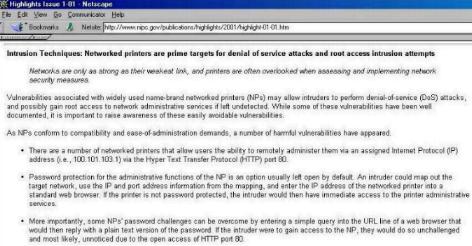 |
Networks are only as strong
as their weakest link, and printers are often overlooked when assessing
and implementing network security measures.
Vulnerabilities associated
with widely used name-brand networked printers (NPs) may allow intruders
to perform denial-of-service (DoS) attacks, and possibly gain root access
to network administrative services if left undetected."
|
.
 |
We have our own example of hacked, and original pages which you can view by clicking on the screen capture to the left. |
 |
In the on-line version of
Chpt 6 of his book, The
Business of the Internet Neil Hannon, notes a link to an article
about Netscape Communications Corp. white paper that deals with the issue
of intranet security and some of its many challenges.
"Cryptography Is The Key To Intranet Security Needs" http://www.techweb.com/se/directlink.cgi?CRN19970630S0089 Copyright (c) 1997 CMP Media Inc.  You can read the original
article on CRN's site at
"There are many challenges in building a full-service intranet that provides safe communications and collaboration. As the exponential growth of the publicInternet demonstrates, TCP/IP solves many problems in a remarkably scalable way. However, TCP/IP was not designed to offer secure communication services. Because TCP/IP was not designed with security in mind, we must bring additional technology and policies to bear to solve typical security problems..." If you go to the web site you can read further about the problems and the cryptographic solutions |
 |
This quiz was
created for another course - students of FCA 240 could try it too since
much of the material os covered herein.
1. Could you explain to someone what the Trojan Horse virus is (as explained in Greenstein text, Chpt 5, page 162) 2. Why do most companies not report IT security situations to authorities? 3. Why are macro viruses so troubling, and how can they be prevented? (as explained in Greenstein text, Chpt 5) |