also known as DDos
Distributed Denial of Service Attacks
- including SYN flooding
this page last updated 2015 Oct 7
- see also the page on
www.witiger.com/ecommerce/hackers.htm

| Denial
of Service Attacks - DoS
also known as DDos Distributed Denial of Service Attacks - including SYN flooding this page last updated 2015 Oct 7 - see also the page on www.witiger.com/ecommerce/hackers.htm |
 |
| Denial
of Service |
Denial
of Service
Sometimes abbreviated as DoS attacks, sometimes referred to as DDoS "DoS attacks are relatively
simple to perform but can have devastating effects. They disable
Web sites and routers by flooding them with false information
requests. In order to discover the source of the requests, technicians
must sort through thousands of lines of computer code. DoS attacks can
last hours or days, depending on how quickly they are detected."
|
| 2015
update |
The
growing threat of DDoS attacks on DNS
http://www.information-age.com/technology/security/123459033/growing-threat-ddos-attacks-dns "Since 2012, the number of infrastructure attacks on the domain name system (DNS) has increased by over 200%. Yet despite this rise, many businesses still arenít doing enough to secure a critical component of their IT infrastructure." Ben Rossi on 17 February 2015 |
| Denial
of Service BASICs |
|
| Denial
of Service |
|
 |
Distributed
Denial of Service Attacks
Essentially DNS attacks done from hijacked computers which means it is difficult for the attacked entity to determine the true source of the threat. When these were first launched,
many were done through networked computers at universities and colleges
making it difficult to trace the individual responsible.
|
 |
SYN
flooding
"The
attacker requests the establishment of a new connection with the target
via a SYN (synchronization) packet. The receiving site, the target in this
case, responds with a SYN/ACK (synchronization/acknowledgement) packet.
At this point, the connection is half-open. The target computer's memory
buffer maintains the information while it waits for the initiating server
to respond with an ACK (acknowledgment) packet and complete the connection.
The final ACK packet is never sent and the connection remains half-open.
If enough of these SYN packets are sent to the targeted site, the memory
buffers become full and legitimate users' SYN packets are unable to get
through"
|
| Denial
of Service Attacks Reported in the Online Media |
Denial
of Service Attacks
First
became known in the general public in February 2000 when several large
sites were crippled, some of them for several hours.
"We are dealing with fact that software products are always buggy, and probably always will be. At the same time, systems are too complex to secure. We actually can't test security to the level we need to. We'll see three or four major bugs in each new version of Windows or Explorer or Java. New products are coming out faster and faster, so we keep losing ground. We've been finding and fixing security bugs in past years, but none of those fixes transfers forward. For all these programs, a new version comes out, the new version is more complex, and there are new bugs." Q:
BusinessWeek - Is there any defense against distributed denial-of-service
attacks?
|
www.cert.org/tech_tips/denial_of_service.html (link still good 2015) CERT is based at Carnegie Mellon University |
CERT publishes
a number of authoritative documents on computer security.
"A recent report from the
CERT Internet security center at Carnegie Mellon University indicated
that denial of service
|
| The CERT Coordination Center is part of the Software Engineering Institute. The Software Engineering Institute is operated by Carnegie Mellon University for the Department of Defense. |
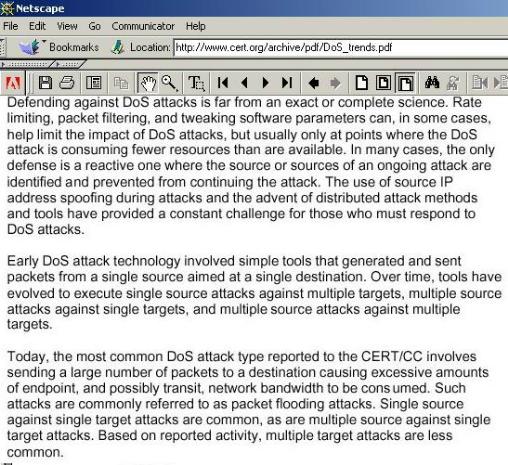 |
In the context of Denial
of Service Attacks, CERT produced a paper in October 2001 which covers
issues on the topic
www.cert.org/archive /pdf/DoS_trends.pdf The CERT paper on DNS was produced by Kevin Houle and George Weaver |
| Denial
of Service Attacks Reported in the Online Media |
Denial
of Service Attacks
"Companies Race To Solve Denial-of-Service Riddle" which was carried in E-Commerce Times formerly at www.ecommercetimes.com/perl/story/7282.html McDonald's short piece centers on some of the new technologies that are helping companies at risk, detect a DOS attack in the beginning and head it off. "Adding to a growing list
of Internet security firms jockeying to establish a viable defense against
costly Denial-of-Service (DoS) attacks, an Internet security firm claimed
Monday that it has developed a new way to detect, trace and block DoS attacks
before they reach their intended online targets. The company, Arbor
Networks of Waltham, Massachusetts,...claims its technology, which uses
'fingerprints' to monitor and
|
| Denial
of Service Attacks Reported in the Online Media Denial
|
Denial
of Service Attacks
"Nine of the 13 computer servers that manage global Internet traffic were crippled by a powerful electronic attack" Oct 2002 "But
most Internet users didn't notice because the attack only lasted an hour.
Its origin was not known, and the FBI and White House were
investigating. One official described Monday's attack as the most
sophisticated and large-scale assault against these crucial computers
in the history of the Internet. Seven of the 13 servers failed to respond
to legitimate network traffic and two others failed intermittently
during the attack, officials confirmed. The FBI's National
Infrastructure Protection Center was "aware of the denial of service attack
and is addressing this matter," spokesman Steven Berry said. Service was
restored after experts enacted defensive measures and the attack
suddenly stopped. The 13 computers are spread geographically across the
globe as precaution against physical disasters and operated by U.S.
government agencies, universities, corporations and private organizations."
"Richard Clarke, President Bush's top cyber-security adviser and head of the protection board, has warned for months [2002] that an attack against the Internet's 13 so-called root server computers could be greatly disruptive. These experts said the attack, which started about 4:45 p.m. EDT Monday, [21 Oct 2002] transmitted data to each targeted root server 30 to 40 times normal amounts. One said that just one additional failure would have disrupted e-mails and Web browsing across parts of the Internet. Monday's attack wasn't more disruptive because many Internet providers and large corporations and organizations routinely store, or "cache," popular Web directory information for better performance. "The Internet was designed to be able to take outages, but when you take the root servers out, you don't know how long you can work without them," said Alan Paller, director of research at the SANS Institute, a security organization based in Bethesda, Md. "
"Although the Internet theoretically can operate with only a single root server, its performance would slow if more than four root servers failed for any appreciable length of time. In August 2000, four of the 13 root servers failed for a brief period because of a technical glitch. A more serious problem involving root servers occurred in July 1997 after experts transferred a garbled directory list to seven root servers and failed to correct the problem for four hours. Traffic on much of the Internet ground to a halt." |
| Denial
of Service Attacks Getting
|
|
| Denial
of Service Attacks Getting
|
example
of an "Alert" sent out by Matrixnetsystems.com in 2002
"This attack began in earnest beginning at approximately 4:00 pm EDT [21 Oct 2002] and is and is ongoing. Several Internet Service Providers (ISPs) have seen an increase in latency coincident with this attack. Matrix NetSystems has advised its clients to temporarily switch traffic from those ISPs most affected by the event. The DNS root servers are given the designations A through M. The most effected include: A VeriSign
Global Registry Services Herndon VA, US
These attacks resulted in periods of zero reachability for many of the root servers and an increase in packet loss approaching 10% from normal packet loss levels of less than 1%. Currently packet loss remains at approximately 4%. At the peak of the attack, average reachability for the entire DNS network dropped below 94% from normal levels near 100%. " |
| Denial
of Service preludes
|
Schneier provides the scenario Burglars come to a warehouse. They cut the connection on the alarm, hoping to trigger a response from the police. The police arrive - see nothing. Property owners representative arrives - sees nothing, everybody leaves. Later that same night, after all the authorities have retreated, the burglars (watching all the time) come back to the premises, break-in again (this time the alarm doesn't go off cause it hasn't been fixed from before) and the bad guys steal everything !!! Schneier goes on further to describe denial of service attacks in detail in Chpt 11 of his book from chpt 11, page 181 "In Sept 1996, an unknown hacker attacked the Public Access Networks Corporation (aka Panix) - which was a New York based internet service provider. What they did was send hello messages (SYN packets) to the Panix computers. What's supposed to happen is for the remote computer to send Panix this hello message, for Panix to respond, and then for the remote computer to continue the conversation. What the attackers did was to manipulate the return address of the remote computers, so Panix ended up trying to synchronize with computers that essentially did not exist. The Panix computers waited 75 seconds after responding for the remote computer to acknowledge the response before abandoning the attempt. The hackers flooded Panix with as many as 50 of these wake-up messages per second. This was too much for the Panix computers to handle, and they caused the computers to crash. This is called SYN flooding, and was the first publicized example of a denial of service attack against an internet host" |
see http://www.witiger.com/ecommerce/hackers.htm for a discussion on DNS attacks using PINGING.
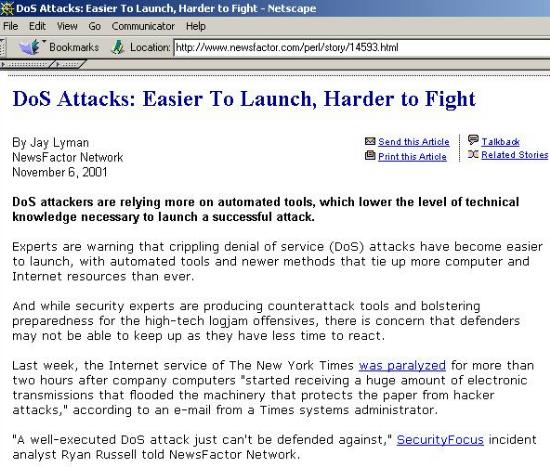
"A recent report from the
CERT center ...indicated that denial of service attacks are getting
easier to create and are having greater impact. "
b
With the circumstances of
Sept 11 - we see a trend around the world for the good guys to try to fight
back - any techniques that work, even "bad guys" techniques.
This raises the question
of using hackers tools to hack back !!!
.n5yn5
On this page there are several
quotes from ecommercetimes.com. Permission was given by Richard Kern, Associate
Publisher of the E-Commerce Times, in an email to Prof. Richardson
2004 Dec 10th, a hard copy of the email is kep on file in Richardson's
permissions binder.
|
|
CONTACT I MAIN PAGE I NEWS GALLERY I E-BIZ SHORTCUTS I INT'L BIZ SHORTCUTS I MKTG&BUSINESS SHORTCUTS I TEACHING SCHEDULE |
| . | |
| MISTAKES ITEXTS USED I IMAGES I RANK IDISCLAIMER I STUDENT CONTRIBUTORS I FORMER STUDENTS I | |
| . |