- location based technology
- applications for marketing in the information age

| RFID
- Radio Frequency
Identification
- location based technology - applications for marketing in the information age |
 |
last
updated 2009 April 07
.
 |
This web page has audio clips - just click on the icon (like the one to the left) and you can hear Prof. Richardson's voice adding additional information to topics on the page. |  |
turn on your speakers to hear audio clips |
| . | This page
used in the following courses taught by Prof. Richardson
.
|
| LEARNING
OBJECTIVES |
After completing
reading this unit, and listening to the lecture in class, student will
have information about:
This page deals with o Introduction
to RFID and its history
|
| HISTORY
and ORIGINS |
RFID stands
for Radio Frequency Identification and was first used 60 years ago today
during WWII.
British planes were then equipped with transponders that emited a pre-determined frequency which could be picked up by other IFF equipped plane. This two way communications allowed other airman to identify each other, as only friendly planes' frequency can be picked up by the IFF receiver, and appear as a blip on the RADAR screen. This system is relatively simple and was not fully refined, but nevertheless, it solved a major identification problem. |
| HISTORY
and ORIGINS |
After the war,
RFID applications and uses slowly trickled down to civilian and commercial
uses.
|
| HISTORY
and ORIGINS |
In the 1970s,
RFID technology was used in cattle tracking and highway toll booths. Cattle
tracking with RFID replaced the traditional method of branding via hot
irons or plastic tags clipped onto ears. This allowed farmers to track
the whereabouts of the cattle and identify their cattle from animals belonging
to other ranchers.
|
| The
TECHNOLOGY of RFID and how it works |
Before learning
how businesses implement and benefit from RFID, it is useful to understand
the technology behind RFID and how it works. This section will present
RFID in layman’s term and allow anyone who is new to the technology
to understand the basic concept and workings of RFID. Technicalities are
kept to a minimum. Details of the technical aspect of RFID are beyond the
scope of this chapter.
The hardware of RFID consists of the following three items:
The word transponder is derived from transmitter/responder and describes how a tag functions - the tag responds to a transmitted signal from the reader. (Tektronix – RFID Overview) Passive tags do not have their own power supply; communication with the reader is caused by minute electrical current or magnetic field induced by the antenna of the reader. The incoming radio frequency carries enough power for the tag to send a response back to the reader for verification and exchange of data. Passive tags can only transmit information over short distances, usually 10 feet or less. Passive tags are relatively inexpensive to manufacture and they are ideal for tracking low cost items. Another advantage of passive tags is their miniscule size – as of 2005, the smallest passive tag measures only 0.4mm X 0.4mm. (www.wikipedia.org – RFID) Many anti-theft systems described in the introduction use passive tags and stationary interrogators. Active tags have their own power supply and can transmit data over long ranges, typically over 100+ feet. The battery can last up to 10 years. They also possess larger storage capacities and can store information from the readers, effectively making them read and write enabled. The information is stored in a non-volatile memory. Usage and application of active tags are infinite such as container shipping tracking or the railroad tracking mentioned earlier. However, due to the embedded battery pack and larger memory, active tags are physically bigger and more expensive than passive tags. Both types of tags contain a unique identifier called Electronic Product Code (EPC), which are preprogrammed by the manufacturer to identify a particular item. This identifier can be picked up by the reader and makes simultaneous readings of many tags possible. (http://www.rfidgazette.org/ - RFID 101) The information stored in the RFID tags is based on PML (Physical Markup Language (PML) – a derivative of the XML (Extensible Markup Language). Readers - An electronic device that uses radio frequency to read or interrogate the tags. When an RFID reader and tag communicate, two things happen – they share energy in the form of radio frequency which allows the exchange of information. (Tektronix; RFID Overview)
|
| The
TECHNOLOGY of RFID and how it works |
Active
tags explained by Shin
Passive tags - explained by Amy with a skit showing an application for "personal" purposes youtube.com/watch?v=0YSHhAhbEDk&feature=related Victor tells a guy how to "track his girlfriend", with an interesting result 
DISCLAIMER - this video does NOT promote stalking nor is it intended to promote violence towards "someone hitting on your girl" |
| The
TECHNOLOGY of RFID and how it works |
Different
types of Radio Frequency used for Communication
Four types of radio frequency are used for communicating between the tag and readers:
Middleware Middleware refers to the hardware, software and technology that collect and process the information generated by RFID. Another name for middleware is Savant. Here is a brief description on how the entire process works:
The software then sort and analyze the data, making it relevant and useful for management decisions, which will be discussed in an example in section 3. |
.
| How
RFID Benefits Business and Customers
|
Students
Jason Niu and Gilbert Chan suggested that you imagine you are the
owner of a Specialty Record Shop who has to deal with, let's say, one hundred
plus new CDs arrival per month. To keep track of your inventory, you probably
have to
1) Count them and write down what the title of each CD is; or 2) Use a bar code scanner and scan each CD's bar code. Now imagine you are a the
sales manager of Wall-Mart or a major CD record shop like HWV where on
a monthly basis you have to deal with millions of crates of goods or tens
and thousands of CDs. How do you keep track of what you have in your The above scenario creates logistic nightmares for many companies. Before we go further on the benefits of RFID in business, we need to have a basic understanding of what the supply chain is. Supply chain is defined as: all suppliers, manufacturing facilities, distribution centers, warehouses, and customers, as well as all raw materials, work-in-process inventory, and finished goods, and all related information and resources involved in satisfying an end-customer's requirements. (www.wikipedia.org – Supply Chain Defined) An improvement in one or
several areas of the supply chain such as more efficient material handling
will reduce the overall cost of the product. The benefit will eventually
trickle down to the customer’s end such as lower prices.
|
| How
RFID Benefits Business and Customers
|
For our [Students
Jason Niu and Gilbert Chan] purpose, we are interested in how RFID
affects the distribution, warehousing and retailers. The supply chain has
a similar characteristic of a dragon boat team. The slowest rower dictates
the overall speed of the entire boat, irregardless how fast the other rowers
can go.
In the supply chain, if it takes a manufacturer only 3 days to manufacture a crate of good and is ready for sale, but distributors takes 1 week to merchandise and inventory, then it will take 10 days before the customer can purchase the good. RFID is set to change this and make the supply chain more responsive to customer demand and reduce slow-downs. Go back to the example of
the Specialty Record Shop where you have to manually scan to keep track
of all the new CDs that comes in for sale. It is a slow, error-prone and
tedious process. This problem gets worse in large retail business like
Wall-Mart, where manually scanning each crate of good is almost impossible.
Hiring a few hundred or a few thousand people whose only job is to scan
and keep track of inventory is economically unfeasible. It is an additional
added cost and burden to the supply chain with no guarantee of speed, accuracy
or reliability. RFID requires no human intervention and can spread out
over large areas – covering the entire warehouse where new shipment
arrivals are instantly scanned and processed. (UPS Supply Chain Solution;
Six Sigma and RFID)
Although 2 minutes on an individual basis may not seem a lot, but what if you have 3000 crates of goods to be scanned and recorded? That is 6000 minutes saved = 100 hours = 4 days! The traditional method stalls the inventory in the warehouse for FOUR full days before they are made available for sale! With RFID, the speed and accuracy is unprecedented. 3000 is only an example, large business like HP, Wall-Mart or online business like www.newegg.com deal with exponentially larger quantities of goods. With RFID cost associated with inventorying and merchandising is reduced, businesses are able to deliver goods faster and cheaper to customers. CRM Buyer has listed a few example on how RFID benefited both consumers and business:
|
| How
RFID Benefits Business and Customers
|
We [Students
Jason Niu and Gilbert Chan] shall end this segment with one hypothetical
example to provide a concrete understanding on how RFID will benefit both
parties:
Black Friday is the busiest
retail shopping day of the year after Thanksgiving. Report shows that after
the crowd disappears from the malls in the long Thanksgiving weekend, a
new phenomena - cyber Monday occurs. Cyber Monday is the equivalent of
Black Friday for online retailers. Many people who return to work after
the holiday continue their shopping spree online ; while at work! (Yahoo
News – Online Retailers await ‘Cyber Monday’)
|
| Implementation of RFID technology in business | . | UTSC
students Jason Niu and Gilbert Chan explain
Implementing RFID in business is a huge financial undertaking and requires a multi-step and multi-facet process. A rushed implementation without careful consideration and evaluation of one’s own business environment will guarantee zero return in investment and a lot of wasted money. Unfortunately, there is no cook-book solution on how a business should implement RFID. Although there are no rulebooks to follow, IBM has developed some general guidelines for businesses to follow when considering implementing RFID: |
| Implementation
of RFID technology in business
IBM's model |
. | 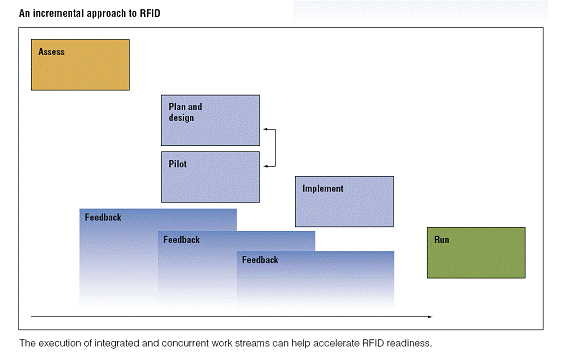
Source: IBM Global Service - Beyond the bar code: Transforming business with Radio Frequency Identification |
| Implementation of RFID technology in business | . | UTSC
students Jason Niu and Gilbert Chan explain
According to IBM's model, the three most important stages in a RFID solution are:
|
| Implementation of RFID technology in business | . | Assess - Not all businesses require a full scale RFID implementation that may cost millions. The business should carefully assess its own needs and choose the appropriate solution that best suits the requirement. For example, the Record Shop may not need expensive active tags to track the physical location of each CD on the shelves or in the warehouse. Maybe all they need is inexpensive passive tags for anti-theft and inventory count. Feedback at this stage is also important, different managers or employees may have different requirements. A sales manager may be interested in how much inventory that is left in the warehouse, while security personnel may want to use RFID to compare quantities of goods shipped vs actual order quantity to ensure accuracy theft prevention. Feedbacks allow the company to choose the best solution that will meet different needs. |
| Implementation of RFID technology in business | . | Plan
& Design - Implementing RFID requires fundamental changes in how
a business uses or process information related to inventory. People affected
by this technology need to be trained and informed.
The information systems should also be retooled to integrated information generated by RFID. For example, the main advantage of RFID is real-time inventory status, but this advantage is totally lost if the sales manager do not have direct access to it, which could be due to reporting structure in a company. Let’s say the sales manager wants a report on how many CDs there are left in the store or warehouse, and he/she has to request this information from another department which have access to the RFID information system. By the time the report reaches the sales manager, it is old data, not real-time data because the actual amount of CDs could have changed in real time. Careful planning and design will avoid such mistakes. |
| Implementation of RFID technology in business | . | Pilot
- after the completion of planning and design, RFID technology should
be incrementally introduced in various areas of the business and carefully
evaluate and benchmark its performance and gather feedback from people
affected by this technology. At the pilot stage, further changes may occur
which requires to go back to the plan and design stage for further fine
tuning.
Finally, a thorough RFID strategy for any company who are considering implementing this technology is recommended by IBM: The types of businesses in today's economy are as diverse as the colors in the kaleidoscope and each of them has different needs and requirements. There is no one size fit all solution. Only with careful planning and assessment will ensure good return on investment and reap the benefits provided by RFID technology. |
| Examples
of how RFID is used today
some applications |
. | Low
-frequency RFID tags are commonly used for animal identification, beer
keg tracking, and automobile key-and-lock, anti-theft systems. Pets are
often embedded with small chips so that they may be returned to their owners
if lost. (Understanding RFID, Tiko Computers Corporation)
High-frequency RFID tags are used in library book or bookstore tracking, pallet tracking, building access control, airline baggage tracking, and apparel item tracking. High-frequency tags are also widely used in identification badges, replacing earlier magnetic stripe cards. These badges need only be held within a certain distance of the reader to authenticate the holder. General Motor's OnStar system, allows instant communications between driver and a human representative. As well, OnStar equipped vehicle can be remotely disabled anywhere in the United States. The technology behind such a safety system is long range Microwave RFID tags. http://searchmobilecomputing.techtarget.com/originalContent/0,289142,sid40_gci924320,00.html?bucket=NEWS |
| Examples
of how RFID is used today
some applications Electronic
|
. | Electronic
Toll routes systems in several places around the world have been using
RFID technology to charge road users.
|
| Examples
of how RFID is used today
some applications the
|
. |
Pallavi wrote
According to SITA ,the
airline industry's IT body, that using RFID in airline baggage tracking
could save airlines up to $1 billion in lost luggage costs. It would reduce
errors in baggage handling from 15% to less than 5%!
Pallavi adds,
|
| Examples
of how RFID is used today some
the
|
. | Pallavi
cautions
One problem to this implementation though is that the RFID tags are still too expensive, they need to be less than 10 cents in order for airlines to seriously considering using them on a large scale, and they are not anywhere near that yet. The other problem is that this technology would have to be implemented at all airports around the world in order for it to be effective and successful. There would definitely be a problem if you had one bag with an RFID tag coming to an airport that didn't use the technology. There would be no way to identify the tag! Pallavi concludes
Source: http://www.silicon.com/research/specialreports/enterprise/0,3800003425,39128136,00.htm |
| Examples
of how RFID is used today
some applications Corporate
|
. | Corporate
Security
http://www.itbusiness.ca/it/client/en/home/News.asp?id=48681&PageMem=3 |
| How RFID benefits you and me | In the emergency room where
every second counts, there is no time to check on a computer for a patient's
medical history. This is especially true when the patient is unconscious
and cannot tell you his or her medical information. Implanted RFID
tags on the human body can help doctors extract your entire medical history
quickly rather you can talk or not, with or without your ID card and possibly,
safe your life. However, privacy issue is a constant concern. source:
http://www.newsfactor.com/news/RFID--Medical-Gain-or-Privacy-Loss-/story.xhtml?story_id=010000FJVJ3S
At the supermarket, some people are very slow at unloading their carts. Some are even slower when they have a lot of times in their cart. After unloading, the cashier usually have to scan in every item manually. However, if there are RFID tags attached to every single item you buy at the store, then there is no physical scanning or unloading needed. The moment you walk through an RFID scanner with your Cart, the supermarket will know exactly what you bought which leaves you, and the people behind you with more time outside of queues. source http://blog.opennetcf.org/ncowburn/RFIDASolutionToSupermarketQueues.aspx(link still works Nov 2006) |
| RFID
and personal
implants (January 2006) |
"under the skin"
devices have been used for several years in animals for a variety of purposes,
such as tracking pets. This application of technology derives from the
1980's when scientists used radio collars for tracking the movements and
activities of a variety of animals. When silicon based devices became smaller
and smaller in the 1990's, it became possible to create some applications
which were small enough to fit under the skin and, in a sense, be part
of the animal's body.
Successful applications of technology devices in animals led to several concepts being applied to humans. |
| RFID
and personal
implants (January 2006) |
Yahoo News described a Canadian named Amal Graafstra who is a 29-year-old (2006) entrepreneur based in Vancouver. Graafstra has RFID chips imbedded in his body and uses these for various IT purposes. Graafstra has chips imbedded that open his front door, with another, he logs onto his computer. Yahoo explains "The computer chips, which cost about $2, interact with a device installed in computers and other electronics. The chips are activated when they come within 3 inches of a so-called reader, which scans the data on the chips. The "reader" devices are available for as little as $50." |
| RFID
and personal
implants (January 2006) |
Graafstra said
at least 20 of his tech-savvy pals have RFID implants.
Yahoo names Mikey Sklar, a 28-year-old Brooklyn resident, who said, "It does give you some sort of power of 'Abracadabra,' of making doors open and passwords enter just by a wave of your hand." Yahoo says "the RFID chip in Sklar's hand, which is smaller than a grain of rice and can last up to 100 years, was injected by a surgeon in Los Angeles." Yahoo explains "Graafstra was drawn to RFID tagging to make life easier in this technological age, but Sklar said he was more intrigued by the technology's potential in a broader sense. In the future, technological advances will allow people to store, transmit and access encrypted personal information in an increasing number of wireless ways, Sklar said. Wary of privacy issues, Sklar said he is developing a fabric "shield" to protect such chips from being read by strangers seeking to steal personal information or identities." Yahoo says "One advantage of the RFID chip, Graafstra said, is that it cannot get lost or stolen. And the chip can always be removed from a person's body." Permission to use the Yahoo! logo and quote from Yahoo! given by Debbie MacLeod, Yahoo! Marketing Manager in email Jan 2005. Copy in the permissions binder. |
| RFID
and personal
implants Graafstra (January 2006) |
http://amal.net/rfid.html, also check http://www.rfidtoys.net/ emailed Graafstra Jan 12th,
2006; received permission to quote, link.
|
| RFID
and personal
implants commercial and business
applications
|
Jordan Ginsberg
of Toronto, interviewed Amal Graafstra about the chip in his hand and in
Ginsberg's story http://p2pnet.net/story/4383
he noted other applications, such as "Spanish clubs offering their VIP
customers the option of receiving an implant that acts as a debit card
so as to avoid carrying a wallet or purse..."
networkworld.com carried
this story September 30, 2004
According to networkworld.com "Morton says the microchip is syringe-injected into one's upper arm and not only acts as a debit card to settle bar tabs, but also allows access into VIP clubs."
|
| RFID
and personal
implants commercial and business
applications
|
Amandeep emailed to say
The company is CityWatchers.com. It provides high-crime areas with cameras and Internet monitoring. The company uses the chips to gain access to data rooms that house videos and images for use by police. The
CEO says that the chips don’t allow the company to track its employees
The
article also states that some morgue workers in Mississippi used the chips
The company that supplied the chips is VeriChip www.verichipcorp.com. On the company website, it also shows some applications of the RFID chips, including infant protection, patient protection, and wander prevention. One application that I found interesting was the infant tracking systems. It’s basically a band with a chip that protects infants from adduction and infant switching. The systems provides full supervision of infants. |
| RFID
and personal
implants medical
|
I have stumbled upon an article about some new implantable RFID technology that can change the lives of over 230 million diabetics. According to the article, the chip is injectable by syringe, when its in your body the chip transmits your body glucose level to a scanner thus eliminating the need for the old painful finger prick technique. The chips are passive so there is no battery required. How cool is that?. Peter says you can read more here rfidgazette.org/2006/10/verichip_sticks.html |
RFID
of Tomorrow
 |
. | The 2006 FIFA Soccer World Cup in Germany used tickets embedded with RFID chips. The new tickets will help defend against counterfeits as well as increase ticket booth efficiency. It's interesting to note that the technology has the ability for organizers to track movements of individual ticket holders, in the interest of riot control for example |
| RFID of Tomorrow | . | A
recent study funded by Wal-Mart and a competing retailer indicates that
RFID tags can help reduce out of stock scenarios by as much as 11%, or
about 3.2% lost.
|
| RFID of Tomorrow | . |
|
| RFID of Tomorrow | . | Roads
& Vehicle Transportation
Similar to the highway 407 transponder in Toronto, Jason Niu says envisage the US mading a license plate with a unique RFID tag serial number, which can be renewed every year online by credit card, that also doubles up as a payment tag for all toll based roads. Potential uses also include private company parking lots to allow access to authorized cars only. Traffic cops can hand out tickets for illegal or expired parking offences. With a single scan, law enforcement officials can track multiple cars and detect any shady activity or registrations. In this area of vehicles, RFID potential use is very deep. (from Understanding RFID, Tiko Computers Corporation) |
| RFID
of Tomorrow
2007 developments |
. | Very
Very small RFID chips
I found something very interesting on the internet today dealing with RFID. The article that I found is called “Be afraid: Powder Sized RFID Chips”. This caught my attention because it sounds very scary and could cause a lot of privacy issues. Apparently Hitachi is making a RFID product that is so small that it’s invisible to the human eye. In order to see this chip, people must look under a microscope to view it. The product size of the tiny RFID is no bigger than a speck of dust at 0.05 x 0.05 mm. Hitachi says it would be used in paper, money, gift certificates and much more to track the item down. The scary part about this powder sized RFID chip is that it could be used on people instead of products. With this being used on people, people wouldn’t even have a clue it’s on them. It could be attached to the persons clothing, skin, or even be swallowed. This would lead to some serious dangerous privacy invasions. Isn’t that scary? |
| RFID
of Tomorrow
2003
|
. | Very
Very small RFID chips
Hitachi explains "...This newly developed version, features an internal antenna...the 0.4mm X 0.4mm chip can thus operate entirely on its own, making it possible to use µ-Chip as RFID IC tags without the need to attach external devices. This breakthrough opens the door to using µ-Chips as RFID IC tags in extremely minute and precise applications that had been impractical until now. For example, the new µ-Chip can be easily embedded in bank notes, gift certificates, documents and whole paper media etc." |
| RFID
of Tomorrow
2007
|
. | Very
Very VERY small RFID chips
Since 2003, Hitachi's RFID
chips have become much smaller.
In 2007, the story Nicholas
found reveals the RFID chip is now measuring
|
| The Challenges & Problems | While
the media have drummed up RFID as the next big thing that can improve businesses,
there are some realities that face companies that stops RFID technology
from entering their businesses.
Economical Challenges: Using current industry trends, the price of RFID tags are still far out of reach for a lot due to costs. Components of an RFID system include the Tags, the readers, and the middleware that helps make sense of all the data. The RFID tags alone, is predicted to hover above 5 cents USD each even until 2008. This is expensive considering the traditional alternative bar codes and scanner solutions.
RFID Tag readers - $500 to $3,000 USD Single RFID Tag – 20 cent to several dollars USD Middleware & Servers - $200,000 USD for a $12 billion manufacturing company http://www.rfidjournal.com/article/articleview/1100/1/2/ (section on Economic Challenges by Jason Niu and Gilbert Chan at U of T ) |
| Problems
Geographical & Technological Challenges |
Geographical
& Technological Challenges:
Standards: Because
RFID tags goes from manufacturer all the way to the retail floor.
There needs to be standards of reading these tags. Similar to languages,
the tags has to be read, written so that everyone can understand.
Unfortunately, there is no global public body that governs frequency standards
used in RFID tags. There are however, national governing bodies, such as
DOC (Department of Communication) for Canada and FCC (Federal Communications
Commission) for the United States. http://www.eweek.com/article2/0,1895,1561854,00.asp
EPCglobal Network is another governing body working with the industry to
set a common standard for RFID to ensure interoperability.
(section on Geographical & Technological Challenges by students Jason Niu and Gilbert Chan at U of T ) |
| Problems | Legal Challenges:
Privacy Issues: A
very simple scenario can describe what people are afraid of about RFID
tags. Assume a criminal has a RFID tag reader; he or she can walk
through a parking lot and scan every car to see if there are expensive
goods inside. Even worse, criminals can scan RFID tags for personal
information if they are even present. The problem with RFID tags
is that they don’t stop emitting signals unless they are located,
and then destroyed. www.computerworld.com/securitytopics/security/privacy/story/0,10801,87286,00.html
|
| Problems
RFID Viruses |
v | It has been
discovered that RFID tags can hold viruses that can be injected into products
in order to acquire information about competitors at an industry level
and personal information at the individual level.
Recently, an experiment at the Amsterdam’s Free University has proved that RFID tags holding a virus can threaten big corporations, such as Wal-Mart, who use the technology to ensure that their stock rooms are filled up with products. The following two articles explain how RFID has become a threat for corporations and individuals: http://www.businessweek.com/technology/content/mar2006/tc20060316_117677.htm
Student Beenish B. at
U of T [UTM] says
Beenish adds
|
| Problems
RFID Viruses |
v | How RFID viruses
can work:
http://www.rfidvirus.org/papers/percom.06.pdf
The RFID tag viruses are very much similar to computer viruses and can be used in an abusive manner by not only individuals and corporations but also by governments as well. Such threats can be done and are harmful to privacy through
Lastly, the article talks about security issues with payment systems as PayPass cards and credit cards like Master card uses the technology, while mobile companies such as Motorola also are planning to implement the "contactless payment systems". |
| Problems
RFID Hacked |
v |
"The information in these
tags could be copied on to another, off-the-shelf tag, which might be used
to impersonate the legitimate holder of the card if a U.S. Department of
Homeland Security agents at the border didn't see the card itself, the
researchers said. Another danger is that the tags can be read from as far
as 150 feet away in some situations, so criminals could read them without
being detected."
|
 |
University of
Toronto (UTM) students Kiel D, Teh Yu H. and Ting Po H. (+ help from Gordon
L) in MGD 415 in April 2009 created a kewl video in which they describe
several components of how Social Engineering tricks can lead to compromising
a RFID access control checkpoint. If you watch the video carefully,
you can pick up on several tricky technical things done with a bit of "fakery".
WTGR says "Thanks , I can see it took a bit of time to create the "script" and plan the shoot, I appreciate your efforts" |
| Problems
RFID vulnerable
|
v |
In closing her email, Tiffany asks "Do you want somebody tracking your movements on Google Maps while you exercise?" with information originally from http://news.cnet.com/NikeiPod-raises-RFID-privacy-concerns/2100-1029_3-6143606.html |
| Problems
RFID adoption
|
v | RFID - adoption
threatened by religious opinions !!
In the first week of February 2007, I received an email from one of my graduate students, Sung L. in the FSM program at Seneca College, and it raised an interesting issue which had never surfaced before. Sung said in their email After reading your section on RFID, I came across a website called Evangelical Outreach which is "dedicated to the proclamation and defense of the gospel of the Lord Jesus Christ". On the website, it describes the Mark of the Beast which has a strong resemblance to the RFID technology. The website quotes a verse from the book of Revelations in the bible, "He also forced everyone, small and great, rich and poor, free and slave, to receive a mark on his right hand or on his forehead so that no one could buy or sell unless he had the mark, which is the name of the beast or the number of his name. This calls for wisdom. If anyone has insight, let him calculate the number of the beast, for it is man's number. His number is 666" (Rev. 13:16-18)... A third angel followed them and said in a loud voice: 'If ANYONE worships the beast and his image and receives his mark on the forehead or on the hand, he, too, will drink of the wine of God's fury, which has been poured full strength into the cup of his wrath" The website then says, " But this mark, which will be universally issued around the entire world, MUST NOT be received under any circumstances, even by Christians!" The student finished their
email suggesting that
|
| Problems
RFID adoption
|
v | RFID - adoption
threatened by religious opinions !!
The email from Sung was "interesting" to say the least so I discussed it with some colleagues and they suggested that this is not a new "reaction" from Christian groups. It was explained that when Bar Codes first came out there were Christian groups who said the same type of thing - meaning that if we are all using barcodes, this must mean the prophecy of Revelations 13 is being fulfilled. I replied to Sung asking for clarification, trying to ascertain if they were advocating a position on this issue of RFID chips, or simply providing some information and it turns out they were only supplying some information. It does raise some interesting questions and I put it on this page so other people can reflect that sometimes we tend to think of technology as being separate from the world of spirituality but in this case we have a good example of how a technological development may be considered, by some people, a bad thing. This suggests that some companies marketing RFID services, and companies using RFID chips might consider preparing themselves for a possible backlash should this concern "get legs". If you want to read the original words of Revelations Chapter 13, you can find it on several websites, such as http://www.bartleby.com/108/66/13.html WTGR |
| Final
Thoughts, for now
(November 2005) |
In this unit,
originally begun by students Jason Niu and Gilbert
Chan, and later added to by oher students, they have outlined the
many benefits and challenges of adopting RFID technology. IBM stated, the
question is not IF we will fully adopt RFID technology, but WHEN.
RFID is not a product or solution; it is an ENABLING technology which will revolutionize our lives and the economy. RFID adoption today (November 2005) is still at its infancy, but by 2010, it is estimated that there will be more than 75 million readers with billions of RFID tags. (Cisco Systems RFID Whitepaper; The RFID Ready Network) The adoption of RFID technology is highly reminiscent of that time when computers were first introduced. In the beginning, very few companies made the hefty investment to computerize their business and these early adopters reaped the benefits. As technology evolved and made computers more affordable, many smaller business and individuals joined the bandwagon to embrace the benefits brought by computers; the same could be said for RFID in the future years to come! |
|
|
CONTACT I MAIN PAGE I NEWS GALLERY I E-BIZ SHORTCUTS I INT'L BIZ SHORTCUTS I MKTG&BUSINESS SHORTCUTS I TEACHING SCHEDULE |
| . | |
| MISTAKES I TEXTS USED I IMAGES I RANK I DISCLAIMER I STUDENT CONTRIBUTORS I FORMER STUDENTS I | |
| . |
©Jason
Niu and Gilbert Chan, Alan Park, Beenish Babary, Amandeep Grewal,
Sung Lee, Tim Richardson
www.witiger.com ![]()