| Privacy Violations
In many countries, people
do not own the information which is collected about them, that is to say,
their personal data.
This information is considered
the property of whatever credit card company, insurance firm, educational
institution that collected the information.
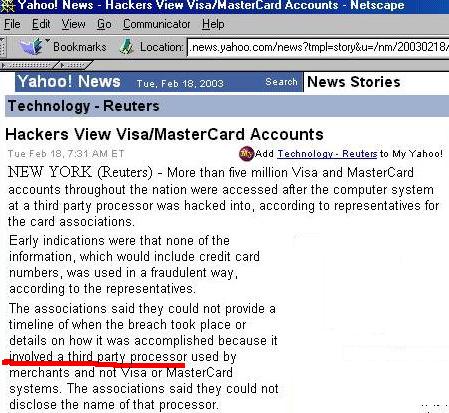
As a consequence of some
outrageous violations of collecting and disseminating personal information,
Canada, New Zealand and other countries have enacted tough laws which are
binding on the companies that collect and pass on personal profile information
(which we noted in Section 1 of this course when we presented the federal
and provincial legislation dealing with this).
Privacy violations are not,
strictly speaking, criminal activity, but, depending on what is done with
the information, it can be used for criminal purposes - such as assuming
an identity for the purposes of obtaining credit, which could then be used
to fraudulently buy products and services.
As a person studying IT security,
it would be your responsibility to understand that protecting the private
personal information of people that have data held within your firm's IT
systems, is critical to conduct effectively and without risk. |










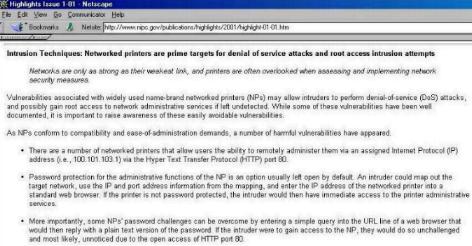
 Printers
vulnerable? - sure.
Printers
vulnerable? - sure.