| National Government's
involved in internet scams
Nigeria

Nigerian Flag
National Government's
involved in internet scams
Nigeria

Nigerian Flag
National Government's
involved in internet scams
Nigeria

Nigerian Flag
|
| . |
In discussing this scam,
we are not making any value judgement on Nigerian people, rather we are
referring to the geographic place where a popular scam format has originated
for many years, and is now becoming very popular using internet communication
means.
WTGR |
.
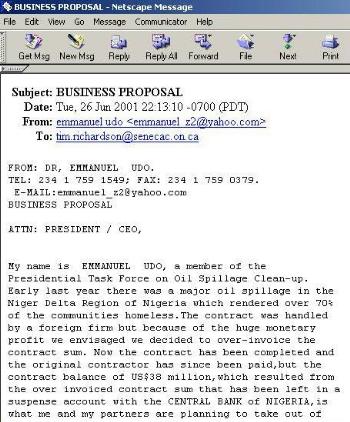 |
For 10 years now, there
have been many scams come out of Nigeria, and with the popularization of
the internet, contact with target victims is facilitated more easily by
email. In the screen capture to the left, you can see an example of an
email that was sent to your professor, attempting to solicit contact.
The best thing to do if you
receive such contact, is pass the information to the RCMP. You should NOT
reply to the person because then they will know they have a "live contact".
You should understand that
they contact thousands and thousands of potential targets and you are nothing
"special" |
 |
From the official web site
of the RCMP |
Most letters are variations
of the following:
-
You receive an "urgent" business
proposal "in strictest confidence" from a Nigerian civil servant /businessman.
-
The sender, often a member of
the "contract review panel", obtained your name and profile through
the Chamber of Commerce or the International Trade Commission.
-
The sender recently intercepted
or has been named beneficiary of the proceeds from real estate, oil
products, over-invoiced contracts, cargo shipments, or other commodities,
and needs a foreign partner to assist with laundering the money.
-
Since their government/business
position prohibits them from opening foreign bank accounts, senders ask
you to deposit the sum, usually somewhere between $25-50 million,
into your personal account.
-
For your assistance, you will
receive between 15-30% of the total, which sits in the Central Bank of
Nigeria awaiting transfer.
-
To complete the transaction,
they ask you to provide your bank name and address, your telephone and
fax numbers, the name of your beneficiary, and, of course, your bank account
numbers.
-
The sender promises to forward
your share within ten to fourteen working days!
It is not true - it is a scam
- DO NOT BECOME A VICTIM. Do not reply, make no contact.
|