

Chpt 3
Chpt 4

Chpt 2
| IEC 818 | SECTION 2 ©
Prevention,
Detection, Reaction
|
changes last made to this page 2001, Aug 01
In Section Two we will use
material from the following texts
 |
Chpt 5 |
 |
Chpt 2
Chpt 3 Chpt 4 |
 |
Chpt 1
Chpt 2 |
| . | Learning Objectives
for Section 2
Section 2 is organized to After completing this section participants will be able to
|

Chpt 5
|
"Electronic Commerce":
Greenstein & Feinman, Chpt 5 The Risks of Insecure Systems
the powerpoints for Chpt
5 can be obtained from
"Until recently, most information security breaches were initiated by insiders. However a study by the CSI Computer Security Institute and FBI indicates that this trend is rapidly changing. The findings indicate that the number of external attacks is growing because if the increased use of the Internet" Overview of Risks Associated
with Internet Transactions
risks associated with transactions between business partners risks associated with confidentially-maintained archival, master file and reference data risks associated with viruses and malicious code overflows (in addition to the information in the Greenstein text, scroll down to viruses) |

Chpt 3 Types of
Types of
|
Secrets &
Lies: Digital Security in a Networked World
by Bruce Schneier Chpt 3 Attacks
|

Chpt 3 Types of
- Frauds |
|

Chpt 3 Types of
- Scams |
Scams
Schneier quotes the National Consumers League (Chpt 3, page 24) "the five most common online scams are
|
 |
Privacy Violations
In many countries, people do not own the information which is collected about them, that is to say, their personal data. This information is considered the property of whatever credit card company, insurance firm, educational institution that collected the information. As a consequence of some outrageous violations of collecting and disseminating personal information, Canada, New Zealand and other countries have enacted tough laws which are binding on the companies that collect and pass on personal profile information (which we noted in Section 1 of this course when we presented the federal and provincial legislation dealing with this). Privacy violations are not, strictly speaking, criminal activity, but, depending on what is done with the information, it can be used for criminal purposes - such as assuming an identity for the purposes of obtaining credit, which could then be used to fraudulently buy products and services. As a person studying ECP 1220, it would be your responsibility to understand that protecting the private personal information of people that have data held within your firm's IT systems, is critical to conduct effectively and without risk. |

Chpt 3 Types of
- Privacy Violations |
Privacy Violations
Schneier, page
29
If the attacker wants to know everything about
As Schneier says, "this attack harnesses the power of correlation" Data harvesting is only worthwhile
doing if it can be automated, and computers allow the automation process
to be done very effectively. Using good cryptography will thwart harvesters
since they will not be easily able to identify if what they are looking
for is in the target they are attacking.
|

Chpt 3 Types of
Types of
|
Secrets
& Lies: Digital Security in a Networked World
by Bruce Schneier Chpt 3 Attacks
Schneier gives an amusing example noting that in the hours leading up to the 1991 bombing of Iraq, pizza deliveries to the Pentagon increased one hundredfold - even if you did not know what the generals and admirals were talking about, it had to be something important from which there would be some serious time spent on decision making.
|
| Internal
Threats |
Internal
Threats
|
| Internal
Threats |
Internal
Threats, Logic Bombs
|
 |
The disgruntled
employee poses but one of many insider threats to information systems
and the valuable data stored therein. Unauthorised access from insiders,
rather than outside hackers, accounted for 44% of network security breaches
last year, according to the March 2000 survey by Computer Security Institute
(CSI) and the FBI.
"The greatest exposure to any organisation is what I call the knowledgeable insider - anybody from a janitor to a vendor or an active or ex-employee," says Steve Dougherty, director of information security at the Fulsom, California-based California Independent System Operator, which is taking over management of power grid transmissions for 27m Californians with the stateís recent industry deregulation. American Society for Industrial Securityís (ASIS). 89% of respondents to the ASIS 1997/1998 Intellectual Property Loss Special Report indicated that their biggest concern regarding system security is retaliation from disgruntled employees.. |
| University
College computers - a weak link |
|
| Risks
With Business Partners they
may
Risks
they
may
|
Microsoft - which one would presume is very very careful about who they partner with, is often vulnerable when the partner makes a bad mistake. Some of these mistakes happen when the intermediary is responsible for dispensing some service, such as making downloads available. In the screen capture below, you can see Prof. Richardson has received an email from SANS. This email details how Microsoft Hotfixes downloaded from the Premier Support and Gold Certified Partner web sites were infected with the Fun Love virus. 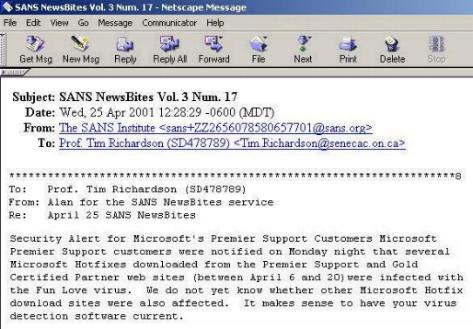 The original email has been
uploaded to the ECP site and you can read the full text, including other
warnings and info at
|
 |
It is not the
intention of this part of the course to be able to adequately cover all
the various types of viruses that may effect e-commerce since do not have
the time nor resources to do that satisfactorly -
but, it is important to have some understanding of the business risk at stake here and try to evaluate if it is a serious problem, because - if it is a serious problem, then every e-commerce professional needs to add to their portfolio of knowledge, some degree of understanding about viruses. |
 |
This web site is very helpful and you are encouraged to bookmark it
and check it for terms you do not know.
|
|
Virus Protection and business risk Virus
|

"IT's Battleground: The Quest for Virus Protection" is the title of an August 4th, 2000 in Computing Canada www.plesman.com/Archives/cc/2000/Aug/2616/cc261614a.html In this August 4rth article
it is noted that
From the August 4rth article "Symantec, publisher of the market-leading Norton Anti-Virus, has seen an average of 115 new viruses each month this year, up 30 per cent from 1999." |
| Viruses | "Virus Vigilance
"
is the title of a December 11, 2000 article in Computerworld written by Deborah Radcliff http://www.surfcontrol.com/news/articles/content/12_11_2000_cw.html In this Dec 2000 article it is noted that "The problem with today's viruses is twofold: Not only can they be easily rewritten to change their signatures and bypass antivirus tools, but they are also tempting attachment types for click-happy users who see nothing wrong with opening mail attachments from trusted sources. " translated 1. viruses can change form so the anti-virus software you installed, and obediently updated, cannot recognize the new virus as a threat, and does not screen it outSo, what is the problem when people don't listen, andfollow proper procedures to protect against viruses? Radcliff quotes Roland Cuny,
chief technology officer at Webwasher.com, an Internet content filtering
vendor
What is part of a technical solution to block viruses? Radcliff quotes experts saying
you can "...set up filters to block executable attachments before they
get to desktops. Blocking file types known to carry viruses and Trojan
horses (hidden programs) may sound extreme. Bruce Moulton, vice president
of infrastructure risk management at Fidelity Investments in Boston said
he first reviewed how his company uses these file types. Once he determined
that these attachments weren't even used for business purposes, making
the decision to block them was easy. "The business impact of shutting out
these file types is zero because 99.9% of these attachments that come in
are for personal viewing, like animated Christmas cards, movie clips,
things like that,"
|
| Worm
Viruses Worm
Worm
Viruses Worm
Worm
Worm
|
.
What does it do? "Code Red, named for a caffeinated soft drink favored by computer programmers, scans the Internet for other computers to infect, and as more computers are infected the scanning gets more widespread and could slow Internet traffic to a crawl. The worm can also defaces
sites, though in two of the three known variants no vandalism
is apparent to computer users. In last week's hits, some U.S. government
sites showed the message ''Hacked by Chinese!'' but the Chinese government
said the worm probably did not come from China."
"Government agencies in Canada and the
United States, as well as academics and Web security experts, were monitoring
the situation closely, but did not detect any slowdown right after the
worm's expected arrival at 8 p.m. EDT., July 31, 2001"
|
| Before we finish the section on viruses, it would be worthwhile to visit the Security Section on Netscape's site. There is a short Q&A about viruses and a helpful glossary. |  |
| Denial
of Service |
Denial
of Service What is DOS?
"DoS attacks are relatively
simple to perform but can have devastating effects. They disable
Web sites and routers by flooding them with false information
requests. In order to discover the source of the requests, technicians
must sort through thousands of lines of computer code. DoS attacks can
last hours or
|
| Denial
of Service |
|
| Denial
of Service Attacks Reported in the Online Media |
Denial
of Service Attacks
First
became known in the general public in February 2000 when several large
sites were crippled, some of them for several hours.
"We are dealing with fact that software products are always buggy, and probably always will be. At the same time, systems are too complex to secure. We actually can't test security to the level we need to. We'll see three or four major bugs in each new version of Windows or Explorer or Java. New products are coming out faster and faster, so we keep losing ground. We've been finding and fixing security bugs in past years, but none of those fixes transfers forward. For all these programs, a new version comes out, the new version is more complex, and there are new bugs." Q:
BusinessWeek - Is there any defense against distributed denial-of-service
attacks?
|
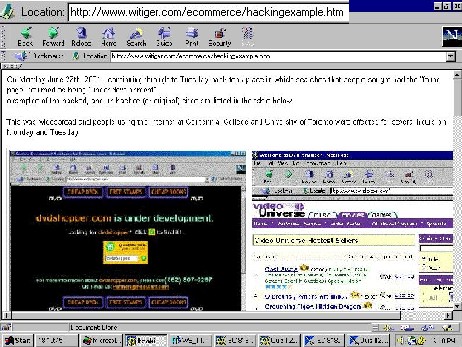 |
We have our own example of hacked, and original pages which you can view by clicking on the screen capture to the left. |
| Denial
of Service Attacks Reported in the Online Media |
Denial
of Service Attacks
"Companies Race To Solve Denial-of-Service Riddle" which was carried in E-Commerce Times www.ecommercetimes.com/perl/story/7282.html McDonald's short piece centers on some of the new technologies that are helping companies at risk, detect a DOS attack in the beginning and head it off. "Adding to a growing list
of Internet security firms jockeying to establish a viable defense against
costly Denial-of-Service (DoS) attacks, an Internet security firm claimed
Monday that it has developed a new way to detect, trace and block DoS attacks
before they reach their intended online targets. The company, Arbor
Networks of Waltham, Massachusetts,...claims its technology, which uses
'fingerprints' to monitor and
|
| Denial
of Service Denial
|
Schneier provides the scenario Burglers come to a warehouse. They cut the connection on the alarm, hoping to trigger a response from the police. The police arrive - see nothing. Property owners representative arrives - sees nothing, everybody leaves. Later that same night, after all the authorities have retreated, the burglers (watching all the time) come back to the premises, break-in again (this time the alarm doesn't go off cause it hasn't been fixed from before) and the bad guys steal everything !!! Schneier goes on further
to describe denial of service attacks in detail in Chpt 11 of his book
from chpt 11, page 181 "In Sept 1996, an unknown hacker attacked the Public Access Networks Corporation (aka Panix) - which was a New York based internet service provider. What they did was send hello messages (SYN packets) to the Panix computers. What's supposed to happen is for the remote computer to send Panix this hello message, for Panix to respond, and then for the remote computer to continue the conversation. What the attackers did was to manipulate the return address of the remote computers, so Panix ended up trying to synchronize with computers that essentially did not exist. The Panix computers waited 75 seconds after responding for the remote computer to acknowledge the response before abandoning the attempt. The hackers flooded Panix with as many as 50 of these wake-up messages per second. This was too much for the Panix computers to handle, and they caused the computers to crash. This is called SYN flooding, and was the first publicized example of a denial of service attack against an internet host" |
The building housing the
offices of POTUS - President of the United States
- is perhaps the most secure
piece of architecture on the planet; the communications are
top secret "state-of-the-art",
and yet, even they are vulnerable to the types of "flooding"
that can be caused by a
DNS attack.
| "Keynote Systems of San Mateo, Calif., a company that monitors Web site performance, said that around 7 a.m. EDT the site began experiencing problems, which it said lasted for about six hours....problems were first noticed at 8 a.m. EDT and that the site was totally blocked for about two hours and 15 minutes. Altogether, he said, the problems lasted for no longer than three hours and 15 minutes. The attack is similar to the February 2000 assaults on popular Web sites such as CNN.com and eBay that effectively shut them down." |  |
 |
In the on-line version of
Chpt 6 of his book, The
Business of the Internet Neil Hannon, notes a link to an article
about Netscape Communications Corp. white paper that deals with the issue
of intranet security and some of its many challenges.
"Cryptography Is The Key To Intranet Security Needs" http://www.techweb.com/se/directlink.cgi?CRN19970630S0089 Copyright (c) 1997 CMP Media Inc.  You can read the original
article on CRN's site at
"There are many challenges in building a full-service intranet that provides safe communications and collaboration. As the exponential growth of the publicInternet demonstrates, TCP/IP solves many problems in a remarkably scalable way. However, TCP/IP was not designed to offer secure communication services. Because TCP/IP was not designed with security in mind, we must bring additional technology and policies to bear to solve typical security problems..." If you go to the web site you can read further about the problems and the cryptographic solutions |
 |
1. Could you explain to someone what the Trojan Horse virus is (as explained in Greenstein text, Chpt 5, page 162) 2. Why do most companies not report IT security situations to authorities? 3. Why are macro viruses so troubling, and how can they be prevented? (as explained in Greenstein text, Chpt 5) |