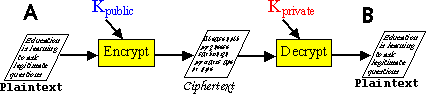Chpt 8
1st ed.

Chpt 10
2nd ed.
Cryptography
Public
Keys
and
Private
Keys

Chpt 8
1st ed.

Chpt 10
2nd ed.
Cryptography
Public
Keys
and
Private
Keys |
Public
Keys and Private Keys
Greenstein
text, page 237 - 239
The
textbook explanation and accompaying diagrams are satisfactory, in addition
there is are online resources that also explain this well.
Public
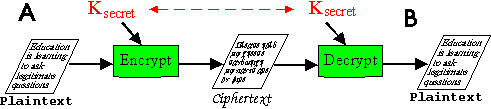
Keys (also known as Asymmetrical Keys)
"Public
Key encryption uses two separate but related keys. One key is used only
to encrypt a message, and its companion key is used to decrypt the
message. Public Key encryption works this way. The person who wants
to receive encrypted files generates a pair of keys in their encryption
program. That person can then 'publish' their public key, or in effect
let anyone and everyone know what their 'public' key is. Anyone who wants
to send this person a message can use this 'Public Key' to encrypt the
message and send it on. When the message is received it can be decrypted
using the secret companion key to the public key. The primary
advantage of Public Key encryption is that you do not have to risk
transmitting a secret key to the person who will receive the message."
from
www.cypost.com/encr_ppkeys.html
 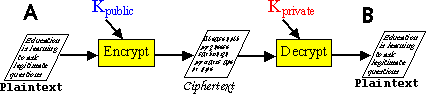
Private
Keys (also called Secret Key or Symmetric Key)
"With
secret-key encryption, both the sender and receiver use the same
key to encrypt and decrypt messages. The two people first agree on a pass
phrase. They should use a different method of communicating than the one
they are going to use to send encrypted messages. They can agree on a password
in person, by phone, or perhaps even communicate a word or phrase known
only to the two of them. A good strong password will include a mix of numbers
lower and upper case letters, and characters; e.g. ad2%56jJ[*92K, since
most brute force attacks will try common dictionary words, names, towns,
dates, etc., or if the person attacking you can get background information
on you they will try combinations that include all your relatives names,
addresses, towns, birthdates, schools, etc. They know that people do have
a propensity for choosing passwords that are somewhat easy to remember.
The encryption software turns the password into a binary number and hashes
it (adds characters to increase the size). Then uses that number(key) to
encrypt all outgoing messages. The mathematical module usedfor encrypting
the message is called the algorithm. The whole system is referred
to as a cipher."
from
www.cypost.com/encr_ppkeys.html
|