Risk
Assessment
Risk
Assessment |
Risk Assessment
 |
Risk Assessment
"How the Pros Help You Probe
the Strength of Your Ramparts"
article written by Dario
Forte, August 1, 2000 |
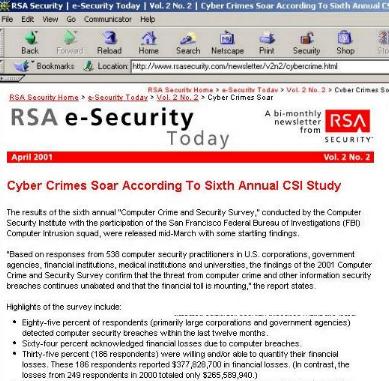
"Most assessments today focus
on the Web user interface, Web server setup, links to company databases,
and server scripts. The checks should include planning of countermeasures
regarding DDoS, defacement, and "hijacking" - the intrusion of a non-authorized
third party into a two-party transaction, as recently occurred at nike.com,
bali.com, and web.net, which were deprived of their virtual identities.
Evaluate the ability of the security analyst to assess Web server setup
vulnerabilities, in terms of administration privileges and software modules
such as CGI, ASP, etc. This analysis is usually performed by a "tiger team,"
which may be made up of ex-crackers or reformed wayward university
students. Or it may consist of properly trained security engineers."
Tiger
Teams |
In the computer industry,
a tiger team is a group of programmers or "reformed" hackers who volunteer,
or are hired, to expose errors or security holes in a web site or network.
They don't simply try to hack their way in, the document the different
methods and attempts they make, and then provide a report to the client
to allow them to know how to fix their vulnerabilities. |
"In every case, a security
assessment service must provide an analysis of the effectiveness of a company's
security controls. Global Integrity, for example, recommends a periodic
assessment based on a review of current documentation, policies,
and practices; interviews with key personnel; and comparisons against industry
"best practices" and other benchmarks. A thorough review should
not stop with the infrastructure. You also need to test your defenses
against social engineering - the set of techniques used to
subvert systems by exploiting human nature. One bank I studied paid no
attention to managing the e-mail relationship with the system administrators.
By spoofing an internal e-mail address, an intruder could contact bank
employees with a request to "check the correct password," and 90 percent
of the time they responded with the correct information without taking
any steps to verify the sender's identity." |